-
FAQs
-
Sysrisk User Manual
-
- Step-by-Step Guide to SysRisk Purchasing Process
- Team or Enterprise License Purchase: Login and Profile Setting Process
- Password Management Process
- Company Profile in SysRisk
- User Creation and Role Assignment in SysRisk
- Customization and Dashboard Configuration
- Homepage Overview
- SysRisk Activity Logs
- Category Management for ERM
- Risk Approval Overview1
- Risk Entry Page for ERM
- Risk Entry Page for PRM
- Creating AI-Generated Risk Entries in SysRisk
- Risk Register Risk Prioritization Page Overview
- Risk Creation, Edit and Approval Process in SysRisk
- Risk Closure Process in SysRisk
- SysRisk Auditing Record Maintenance
- Risk Notification Settings
- Show Remaining Articles (3) Collapse Articles
-
-
Risk Management
-
- Control Risk
- ERM
- Inherent Risk
- Qualitative Risk Analysis
- Quantitative Risk Analysis
- Residual Risk
- Risk Acceptance
- Risk Acceptance Criteria
- Risk Aggregation
- Risk Analysis
- Risk Analysis Methods
- Risk Analytics
- Risk Appetite
- Risk Appetite Framework
- Risk Appetite Statement
- Risk Assessment
- Risk Assessment Matrix
- Risk Assessment Process
- Risk Attribution
- Risk Avoidance
- Risk Bearing Capacity
- Risk Benchmarking
- Risk Capacity
- Risk Capital
- Risk Clustering
- Risk Communication
- Risk Communication Plan
- Risk Concentration
- Risk Contingency
- Risk Contingency Plan
- Risk Control
- Risk Convergence
- Risk Criteria
- Risk Culture
- Risk Dashboard
- Risk Dependency
- Risk Diversification
- Risk Escalation
- Risk Escalation Path
- Risk Evaluation
- Risk Exposure
- Risk Financing
- Risk Framework
- Risk Governance
- Risk Heat Map
- Risk Horizon
- Risk Identification
- Risk Indicator
- Risk Intelligence
- Risk Interdependency
- Risk Inventory
- Risk Landscape
- Risk Management(RM)
- Risk Management Dashboard
- Risk Management Framework
- Risk Management Maturity
- Risk Management Plan
- Risk Management Policy
- Risk Mapping
- Risk Matrix
- Risk Maturity
- Risk Mitigation
- Risk Mitigation Plan
- Risk Mitigation Strategy
- Risk Model
- Risk Monitoring
- Risk Optimization
- Risk Owner
- Risk Ownership
- Risk Policy
- Risk Portfolio
- Risk Prioritization
- Risk Profile
- Risk Quantification
- Risk Reduction
- Risk Register
- Risk Register Update
- Risk Reporting
- Risk Resilience
- Risk Response
- Risk Response Plan
- Risk Review
- Risk Review Process
- Risk Scenario
- Risk Scenario Analysis
- Risk Scenario Planning
- Risk Scoring
- Risk Sensing
- Risk Sharing
- Risk Strategy
- Risk Taxonomy
- Risk Threshold
- Risk Tolerance
- Risk Tolerance Level
- Risk Transfer
- Risk Transparency
- Risk-Adjusted Return
- Show Remaining Articles (82) Collapse Articles
-
- Business Continuity Risk
- Capital Risk
- Competition Risk
- Compliance Risk
- Counterparty Risk
- Credit Risk
- Credit Spread Risk
- Currency Risk
- Cybersecurity Risk
- Deflation Risk
- Environmental Risk
- Ethical Risk
- Event Risk
- Financial Risk
- Foreign Exchange Risk
- Fraud Risk
- Geopolitical Risk
- Health and Safety Risk
- Human Capital Risk
- Inflation Risk
- Infrastructure Risk
- Innovation Risk
- Insurance Risk
- Intellectual Property Risk
- Interest Rate Risk
- Legal Risk
- Liquidity Risk
- Market Risk
- Model Risk
- Natural Disaster Risk
- Operational Risk
- Outsourcing Risk
- Political Risk
- Product Liability Risk
- Project Risk
- Regulatory Change Risk
- Regulatory Risk
- Reputation Risk
- Reputational Risk
- Resource Risk
- Sovereign Risk
- Strategic Alliance Risk
- Strategic Risk
- Supply Chain Risk
- Sustainability Risk
- Systemic Risk
- Technological Risk
- Technology Risk
- Show Remaining Articles (33) Collapse Articles
-
SysRisk offers a comprehensive logging system to track all user activities, ensuring transparency and accountability. Logs are categorized based on roles and specific functions, helping monitor user interactions, administrative actions, and changes to risk entries. There are three primary types of logs: Administrative Logs, User Logs, and Risk Logs, with a special Issue Log for materialized risks.
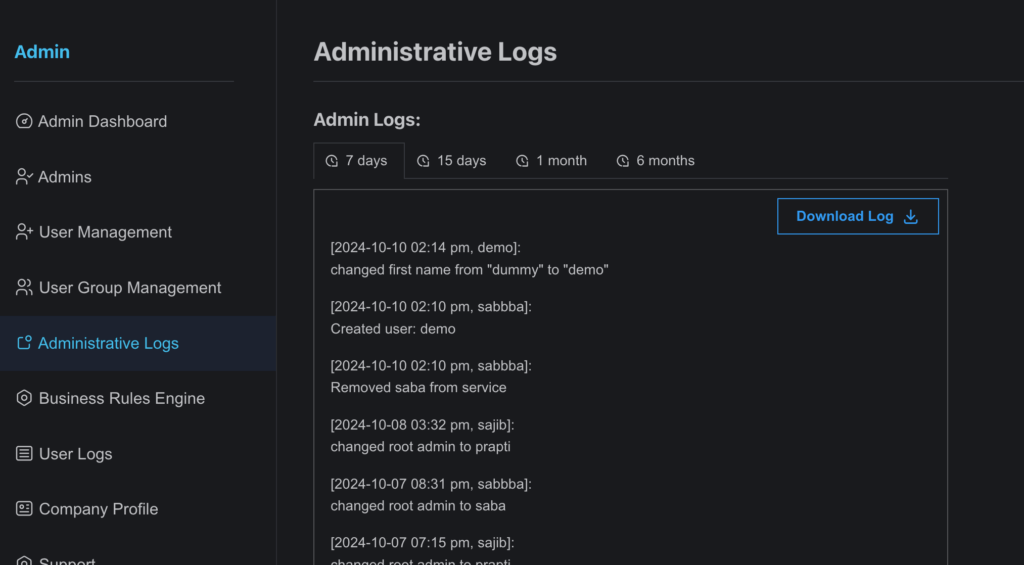
- Administrative Logs
- Access: Available only to Admins.
- Location: Located on the Administrative Log page in the admin module.
- Details: Admins can view a detailed log of all administrative activities performed over the last six months. This includes actions like user creation, updates, removals, adding/removing users from different features, and other adminspecific operations.
Example: Monitoring user management or role assignments.
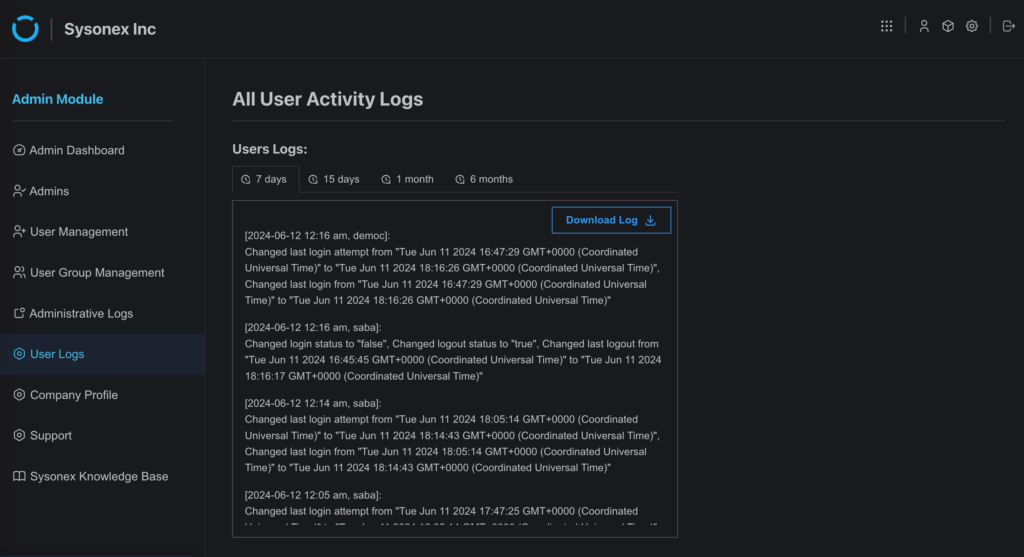
- User Logs
- Access: Available only to Admins.
- Location: Found on the User Logs page in the admin module.
- Details: User logs provide a full record of every activity performed by any user, including product admins, within the system. Each action is logged with precise date and time stamps, enabling detailed monitoring of user interactions with SysRisk.
Example: Tracking login times, risk entry creation, and system changes.
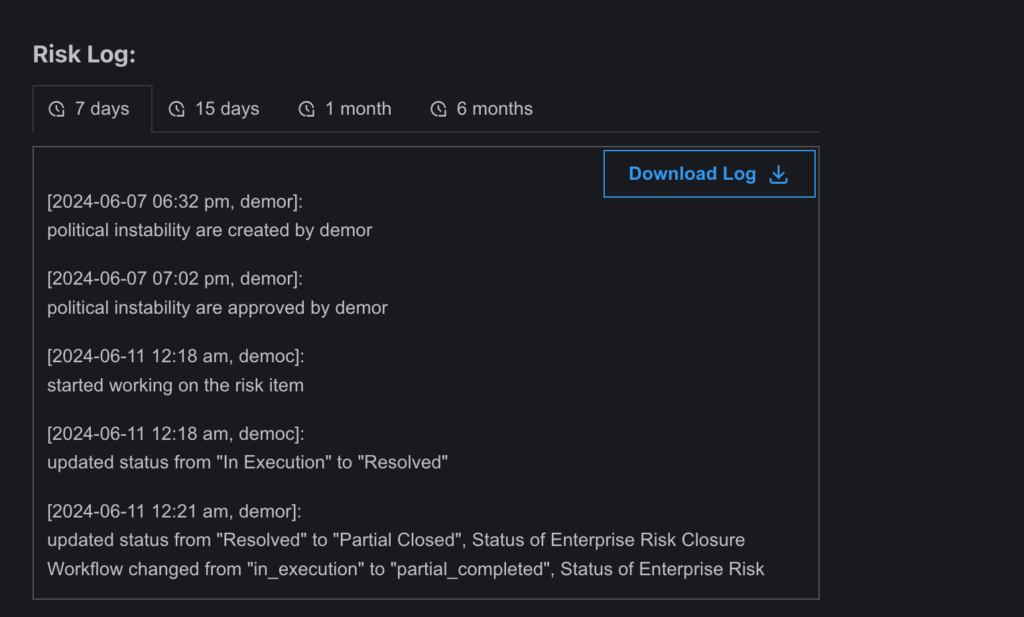
- Risk Logs
- Access: Accessible to all users with the appropriate permissions.
- Location: Embedded in the Risk Register or Risk Prioritization pages, available within the action option of any risk entry. Scroll to the end of the subpage to find the log.
- Details: The risk log provides a complete history of every action taken on a specific risk entry by users involved. Each modification, status update, or comment is tracked to maintain a full record of the risk’s lifecycle.
Example: Monitoring edits, approvals, and status changes of a risk entry.
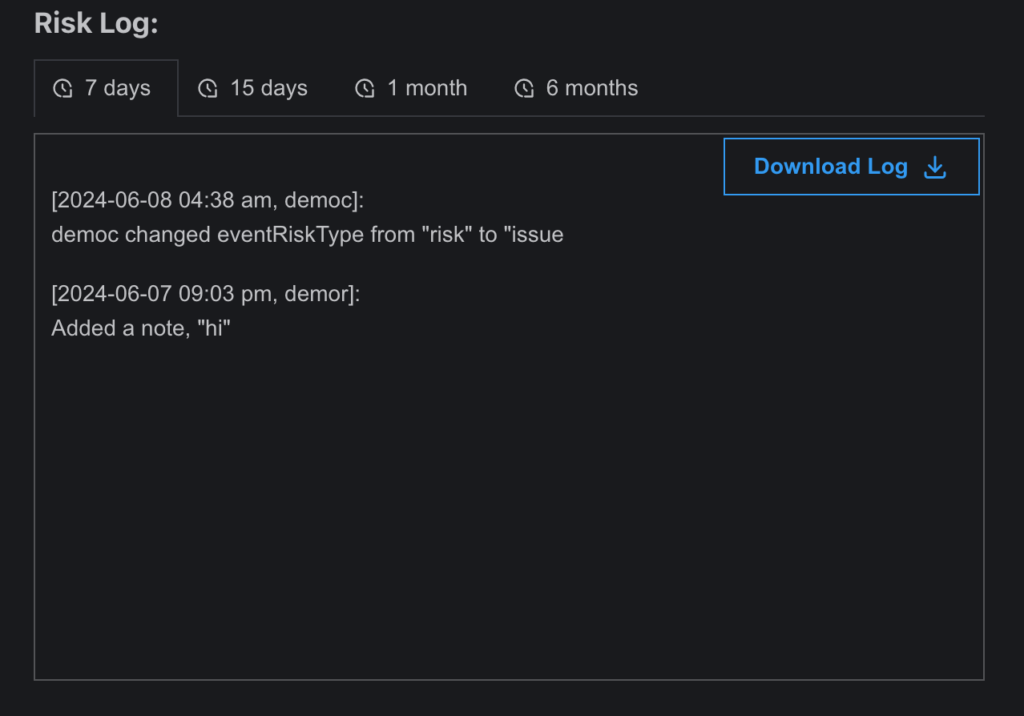
- Issue Logs
- Functionality: Operates similarly to Risk Logs.
- Location: Found in the Issue Register page, under the action option of any issue item. Scroll to the end of the subpage to view the issue log.
- Details: When a risk is raised as an issue, the risk log transitions into an issue log, recording all updates and actions from the moment it is flagged as an issue. The log ensures full traceability of how the issue is managed over time.
Example: Capturing actions like status changes, issue resolutions, and communication updates.
5. Activity Timeline
- Access: Available to all users
- Location: Located in the My Profile module
- Details: The Activity Timeline is a personal log visible to each user, displaying a chronological history of their own interactions within the platform. Activities such as logins, logouts, password changes, and personal information updates are recorded here.
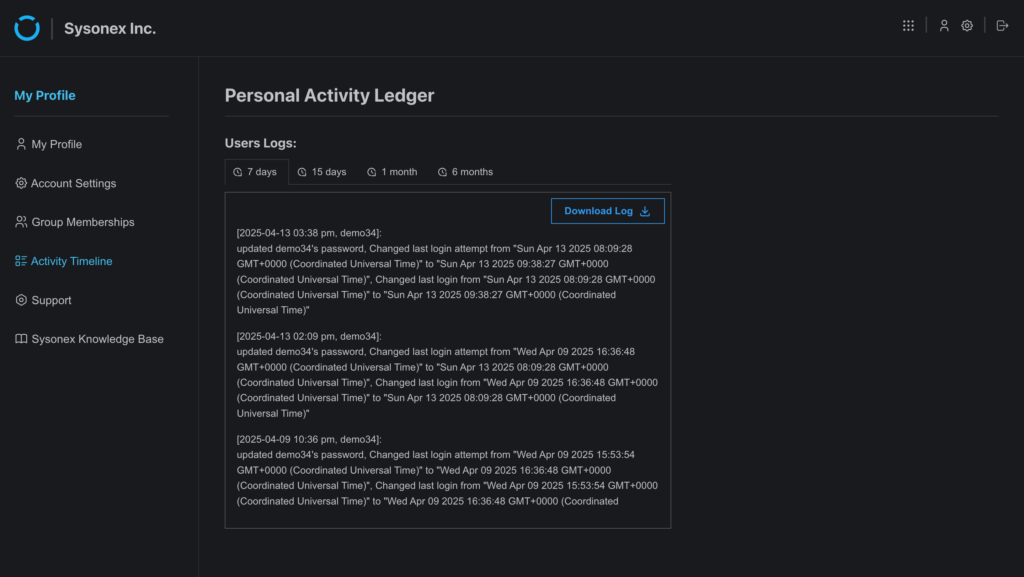
Example: Reviewing personal login times or tracking changes made to profile details
Summary of Logs:
- Administrative Logs: Admin actions over 6 months, user management, feature control.
- User Logs: Activity tracking for users and product admins, including login and system interaction data.
- Risk Logs: Perrisk logs detailing every action taken on risk entries.
- Issue Logs: Logs specific to materialized risks, documenting all changes and actions taken on issue items.
- Activity Timeline: Individual user activity log within the My Profile module.
These logs help SysRisk maintain transparency, ensure accountability, and facilitate effective risk management.
