-
FAQs
-
Sysrisk User Manual
-
- Step-by-Step Guide to SysRisk Purchasing Process
- Team or Enterprise License Purchase: Login and Profile Setting Process
- Password Management Process
- Company Profile in SysRisk
- User Creation and Role Assignment in SysRisk
- Customization and Dashboard Configuration
- Homepage Overview
- SysRisk Activity Logs
- Category Management for ERM
- Risk Approval Overview1
- Risk Entry Page for ERM
- Risk Entry Page for PRM
- Creating AI-Generated Risk Entries in SysRisk
- Risk Register Risk Prioritization Page Overview
- Risk Creation, Edit and Approval Process in SysRisk
- Risk Closure Process in SysRisk
- SysRisk Auditing Record Maintenance
- Risk Notification Settings
- Show Remaining Articles (3) Collapse Articles
-
-
Risk Management
-
- Control Risk
- ERM
- Inherent Risk
- Qualitative Risk Analysis
- Quantitative Risk Analysis
- Residual Risk
- Risk Acceptance
- Risk Acceptance Criteria
- Risk Aggregation
- Risk Analysis
- Risk Analysis Methods
- Risk Analytics
- Risk Appetite
- Risk Appetite Framework
- Risk Appetite Statement
- Risk Assessment
- Risk Assessment Matrix
- Risk Assessment Process
- Risk Attribution
- Risk Avoidance
- Risk Bearing Capacity
- Risk Benchmarking
- Risk Capacity
- Risk Capital
- Risk Clustering
- Risk Communication
- Risk Communication Plan
- Risk Concentration
- Risk Contingency
- Risk Contingency Plan
- Risk Control
- Risk Convergence
- Risk Criteria
- Risk Culture
- Risk Dashboard
- Risk Dependency
- Risk Diversification
- Risk Escalation
- Risk Escalation Path
- Risk Evaluation
- Risk Exposure
- Risk Financing
- Risk Framework
- Risk Governance
- Risk Heat Map
- Risk Horizon
- Risk Identification
- Risk Indicator
- Risk Intelligence
- Risk Interdependency
- Risk Inventory
- Risk Landscape
- Risk Management(RM)
- Risk Management Dashboard
- Risk Management Framework
- Risk Management Maturity
- Risk Management Plan
- Risk Management Policy
- Risk Mapping
- Risk Matrix
- Risk Maturity
- Risk Mitigation
- Risk Mitigation Plan
- Risk Mitigation Strategy
- Risk Model
- Risk Monitoring
- Risk Optimization
- Risk Owner
- Risk Ownership
- Risk Policy
- Risk Portfolio
- Risk Prioritization
- Risk Profile
- Risk Quantification
- Risk Reduction
- Risk Register
- Risk Register Update
- Risk Reporting
- Risk Resilience
- Risk Response
- Risk Response Plan
- Risk Review
- Risk Review Process
- Risk Scenario
- Risk Scenario Analysis
- Risk Scenario Planning
- Risk Scoring
- Risk Sensing
- Risk Sharing
- Risk Strategy
- Risk Taxonomy
- Risk Threshold
- Risk Tolerance
- Risk Tolerance Level
- Risk Transfer
- Risk Transparency
- Risk-Adjusted Return
- Show Remaining Articles (82) Collapse Articles
-
- Business Continuity Risk
- Capital Risk
- Competition Risk
- Compliance Risk
- Counterparty Risk
- Credit Risk
- Credit Spread Risk
- Currency Risk
- Cybersecurity Risk
- Deflation Risk
- Environmental Risk
- Ethical Risk
- Event Risk
- Financial Risk
- Foreign Exchange Risk
- Fraud Risk
- Geopolitical Risk
- Health and Safety Risk
- Human Capital Risk
- Inflation Risk
- Infrastructure Risk
- Innovation Risk
- Insurance Risk
- Intellectual Property Risk
- Interest Rate Risk
- Legal Risk
- Liquidity Risk
- Market Risk
- Model Risk
- Natural Disaster Risk
- Operational Risk
- Outsourcing Risk
- Political Risk
- Product Liability Risk
- Project Risk
- Regulatory Change Risk
- Regulatory Risk
- Reputation Risk
- Reputational Risk
- Resource Risk
- Sovereign Risk
- Strategic Alliance Risk
- Strategic Risk
- Supply Chain Risk
- Sustainability Risk
- Systemic Risk
- Technological Risk
- Technology Risk
- Show Remaining Articles (33) Collapse Articles
-
Risk Register Overview
The Risk Register Page is the central repository for all approved risk entries in SysRisk, allowing for the seamless tracking and management of risks. Each risk entry, upon approval, receives a unique ID for easier reference. This page is essential for the monitoring, updating, and analyzing of risks, providing admins, product admins, and authorized users with the tools to make informed decisions and track ongoing risks.
- Centralized Risk Data:
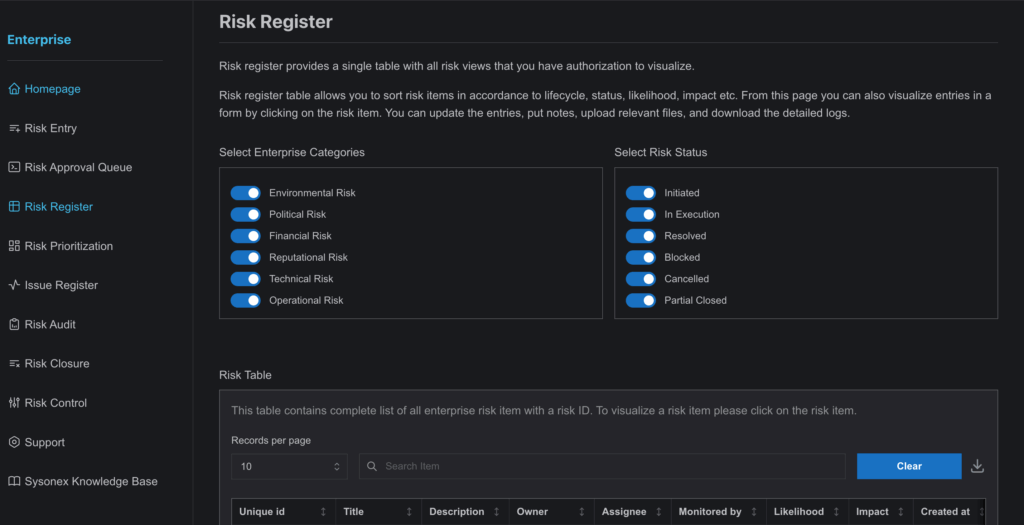
- All approved risks, along with their associated details, are stored in the Risk Register.
- Admins and product admins have access to all risk entries within the module, while general users can only view risks they are assigned to.
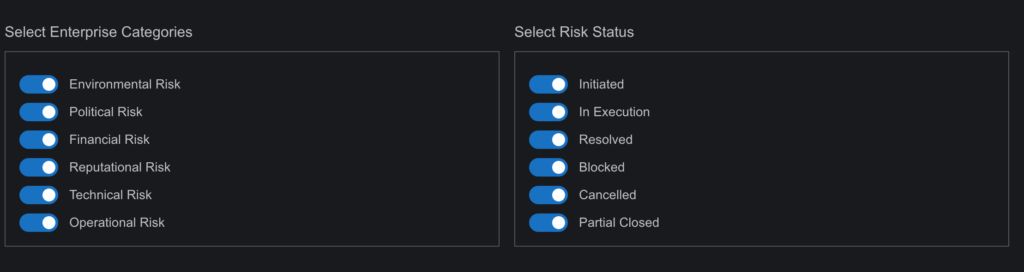
- Comprehensive Filtering and Search Options:
- Risks can be filtered by their categories/project/framework names and status (e.g., “Initiated”, “In Execution”, etc.), and a search bar allows for easy retrieval of specific risks.
- Risk Editing:
- Although a risk entry cannot be deleted, it remains editable after being recorded in the register. Users can update risk information, track progress, and make necessary changes.

- Status Management:
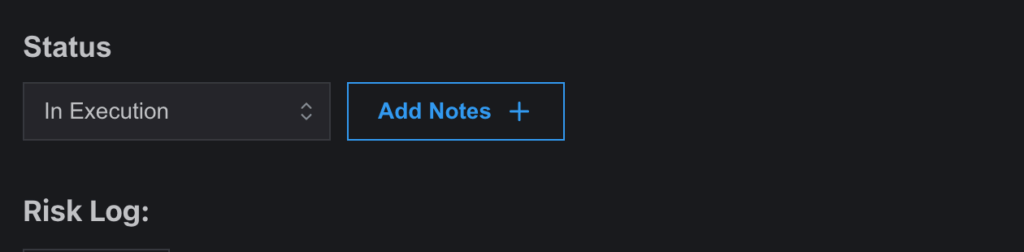
- When a risk is first approved, its status is set to “Initiated.”
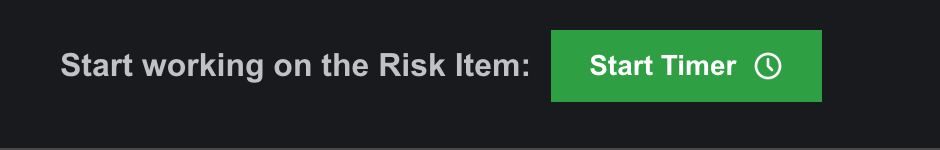
- To update the status to “In Execution”, users can start the timer on the edit subpage. Alternatively, statuses can be updated manually.
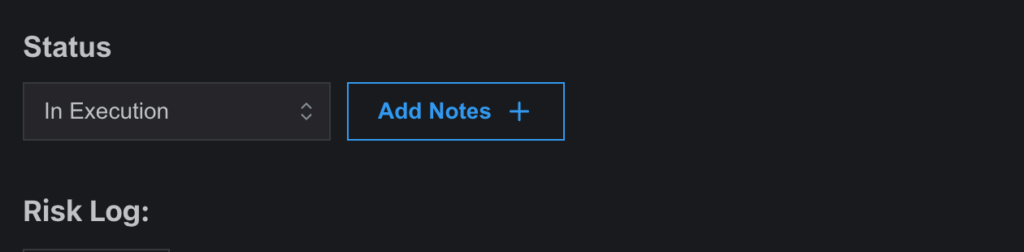
- Risks can be marked as “Resolved”, and the closure request can be submitted. Until officially closed by the assigned user, the risk will appear as partially closed.

- Risk Closure:
- Once resolved and approved for closure, the risk status updates to “Closed”, after which the risk remains in the register for seven years for reference.
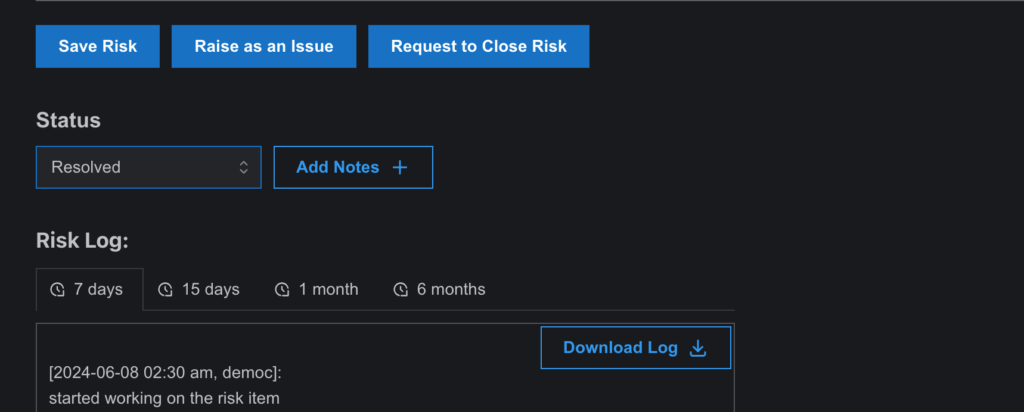
- Note Addition:
- Users can add notes for suggestions, corrections, or additional information from teammates, fostering collaborative risk management.
- Document Management:
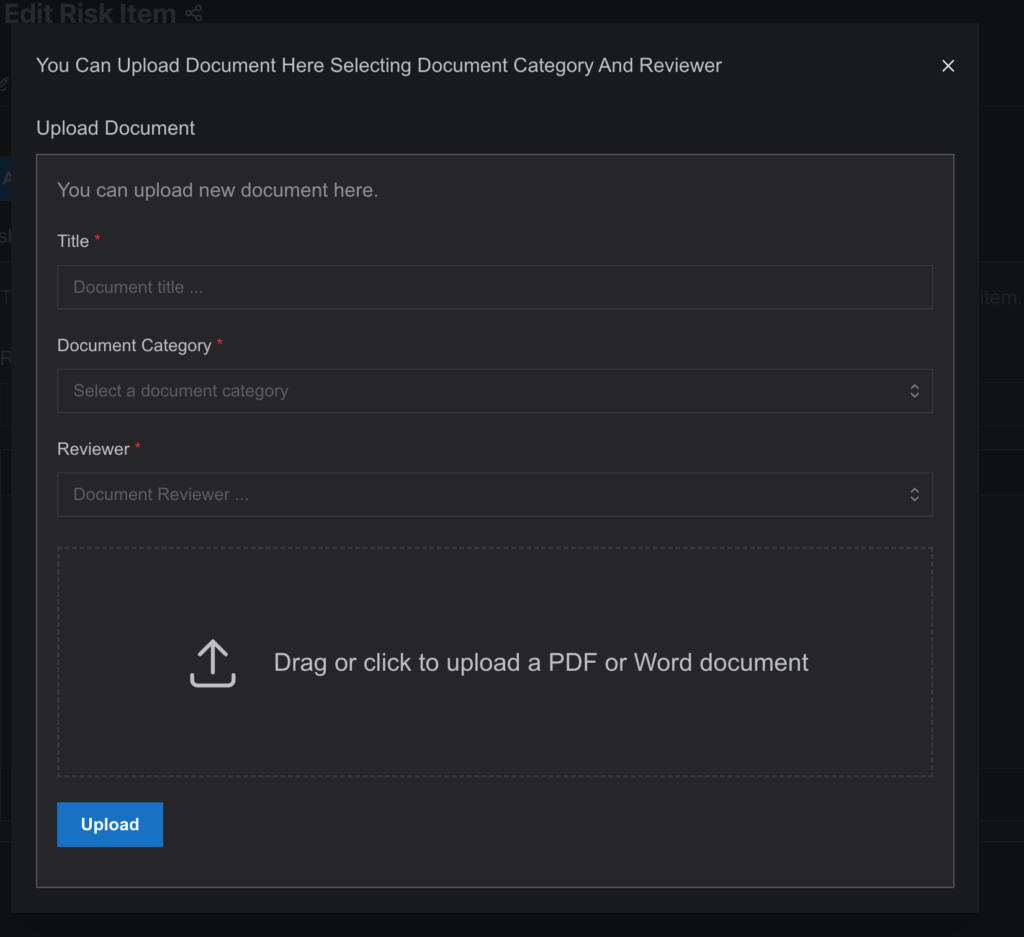
Within the Edit Risk side drawer, users can upload PDF or Word files related to specific risks through the Add Document tab.
- Navigate to the Add Document
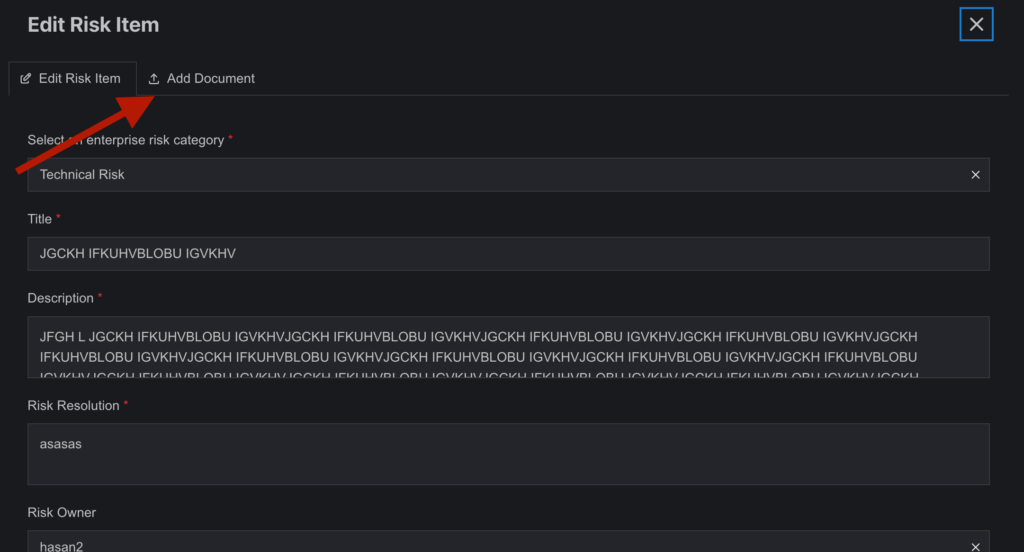
2. Click on Add Document to open a form with relevant upload fields.
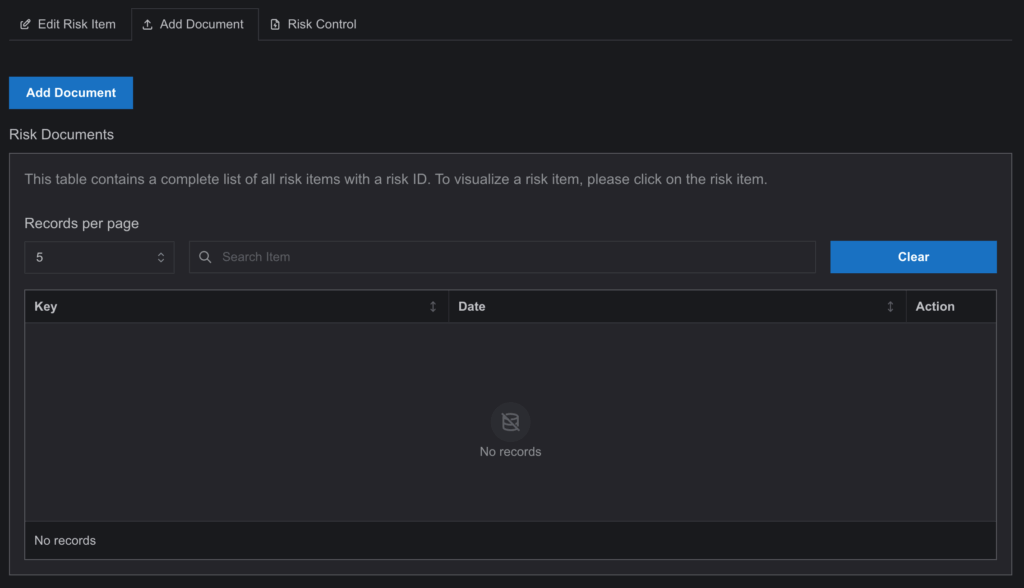
3. Fill in the Title field, then select the Category and Reviewer—both of which are predefined in the Document Management page. The Category dropdown displays options linked to the risk’s category or project, while the Reviewer list includes users already added to that document category.
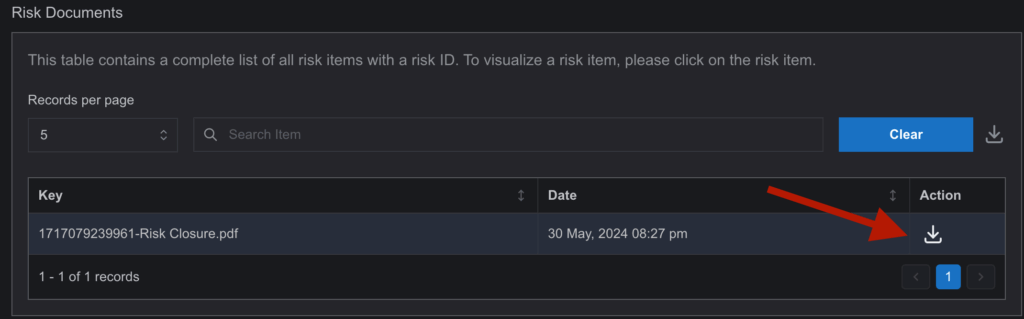
4. Once uploaded, the document will appear in a table where it can be downloaded or deleted for future operations.
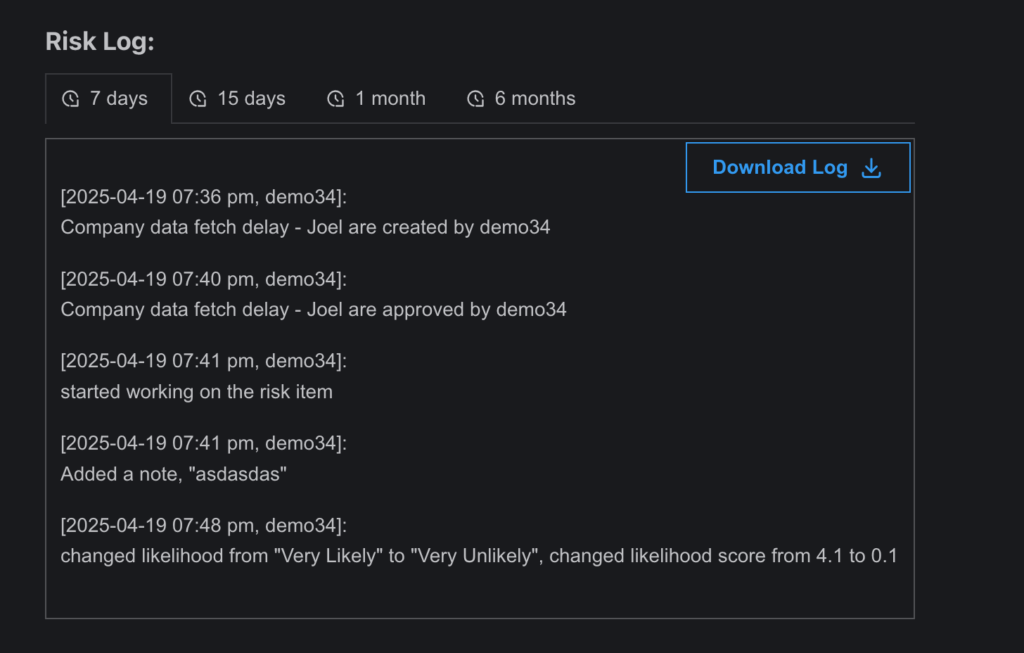
- Risk Log:
- Every action taken on the risk item is recorded in the Risk Log, offering full traceability and transparency.
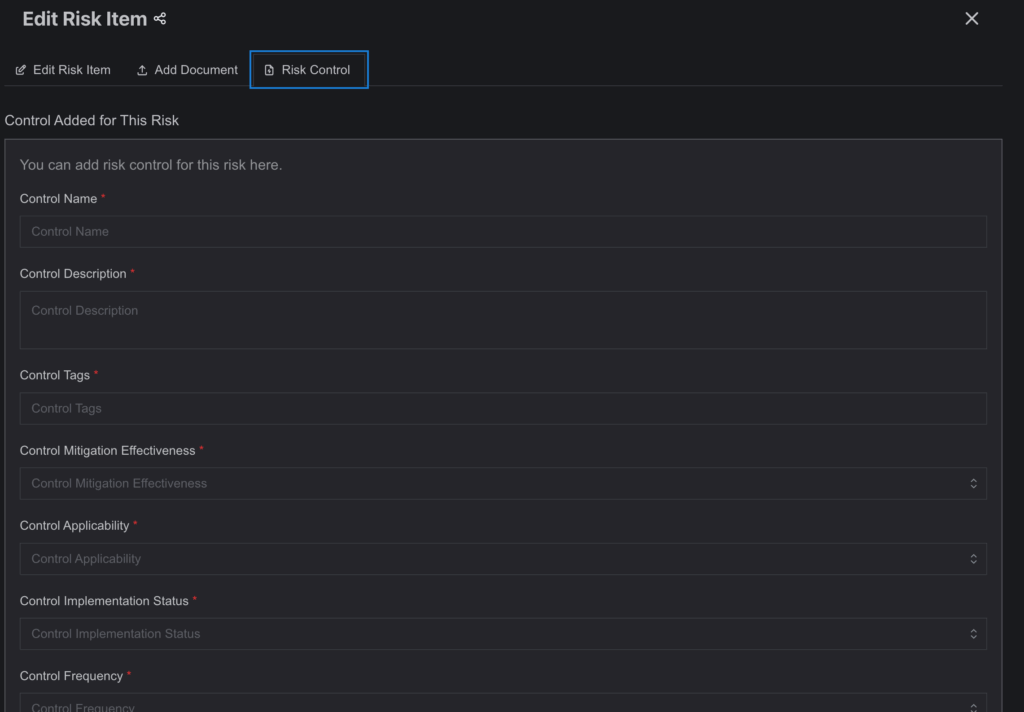
- Risk Control:
Within the Edit Risk side drawer, users can define specific controls to mitigate a risk through the Risk Control tab.
Navigate to the Risk Control tab.
Click on Risk Control to open a structured form for entering control details.
Fill in the following required fields to define a new control:
- Control Name: Enter a descriptive name for the control being applied.
- Control Description: Provide a brief explanation of what the control does and how it addresses the risk.
- Control Tags: Add relevant keywords to help categorize or search the control later.
- Control Mitigation Effectiveness: Select the effectiveness level of the control (e.g., Low, Medium, High), which affects the residual risk calculation.
- Control Applicability: Specify whether the control is fully or partially applicable to the selected risk.
- Control Implementation Status: Indicate the current implementation status such as Planned, In Progress, or Implemented.
- Control Frequency: Choose how often the control is executed (e.g., Daily, Monthly, Annually).
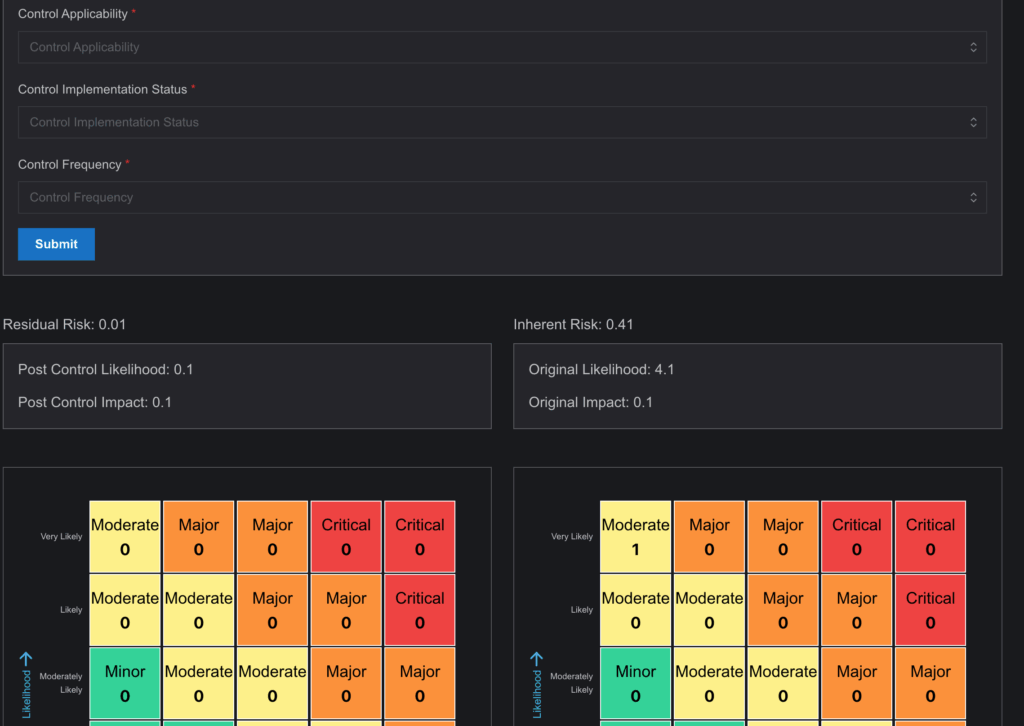
After filling out all fields, click Submit.
Once submitted, the system automatically updates the Residual Risk, recalculating values for Post Control Likelihood and Post Control Impact based on the entered control data. These updates are visually reflected in the risk matrix, showing the difference between Inherent Risk (before control) and Residual Risk (after control).
The applied control will be linked to the selected risk for future reference, audit tracking, and compliance review.
Risk Prioritization Page Overview
The Risk Prioritization Page is a powerful feature in SysRisk that allows users to assess and rank risks based on several criteria, such as impact, likelihood, and cost priority. This page helps organizations focus their efforts on managing the most critical risks, making the best use of available resources.
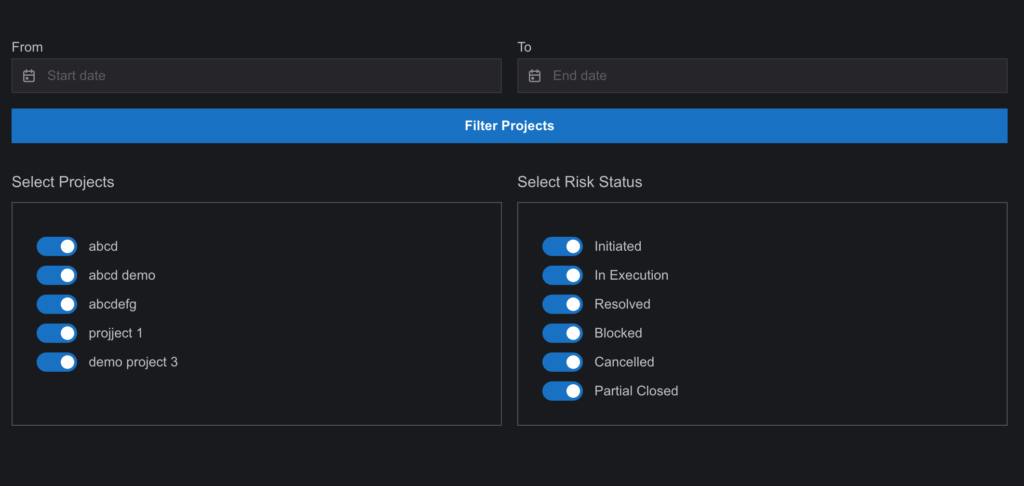
- Time Filter (PRM Module):
- Users can filter projects by specific time periods to focus on risks relevant to a particular window of time.
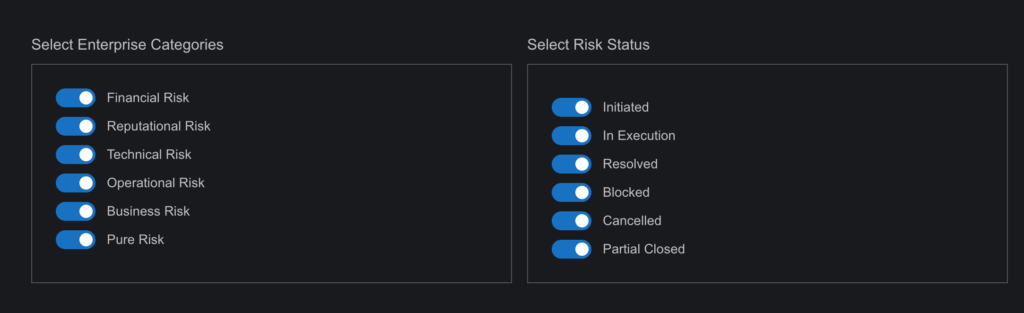
- Category and Status Filters (ERM Module):
- SysRisk offers filters for risk categories and activity status, allowing for an organized view of prioritized risks.
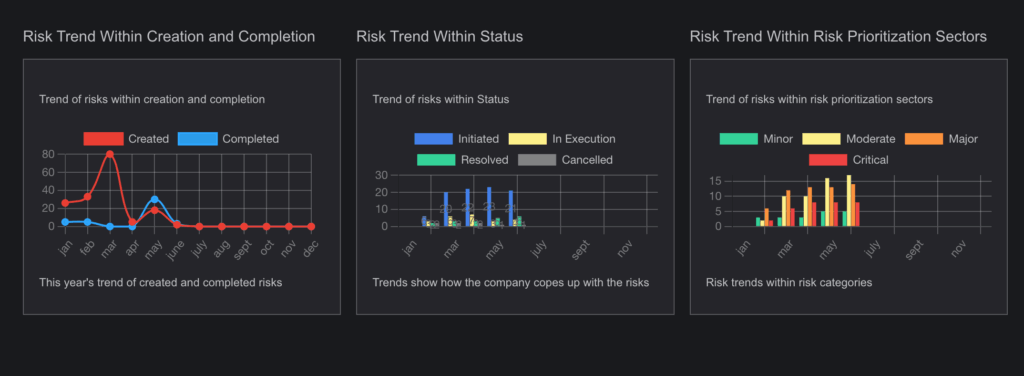
- Visual Representation:
- Risks are presented with graphs, heat maps, and other visual tools to provide a clear understanding of their priority.
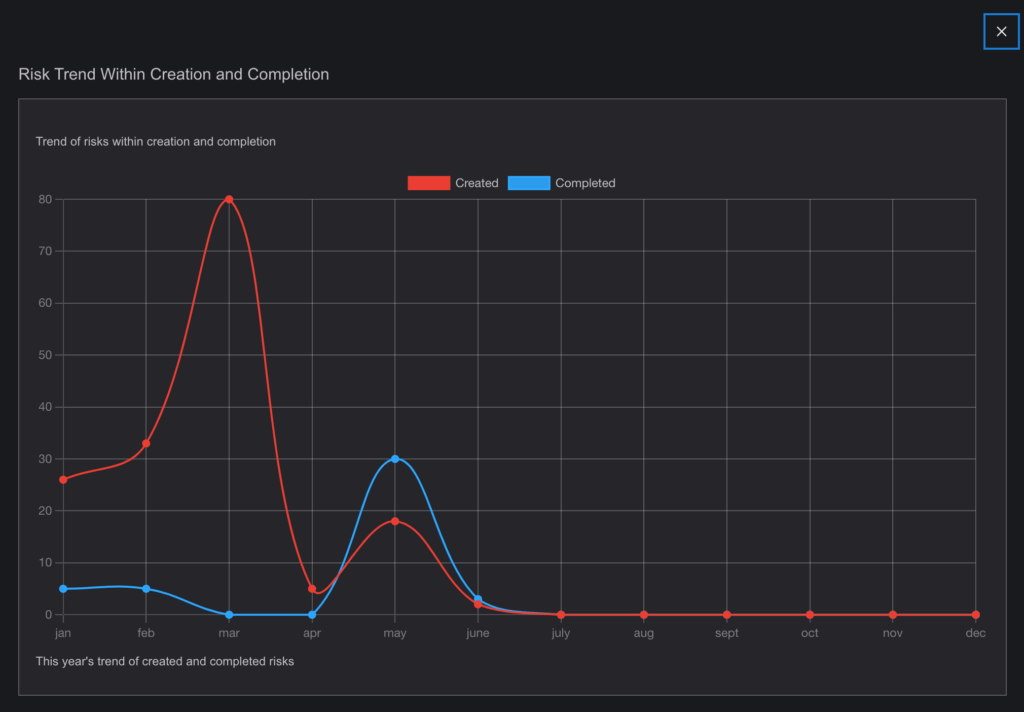
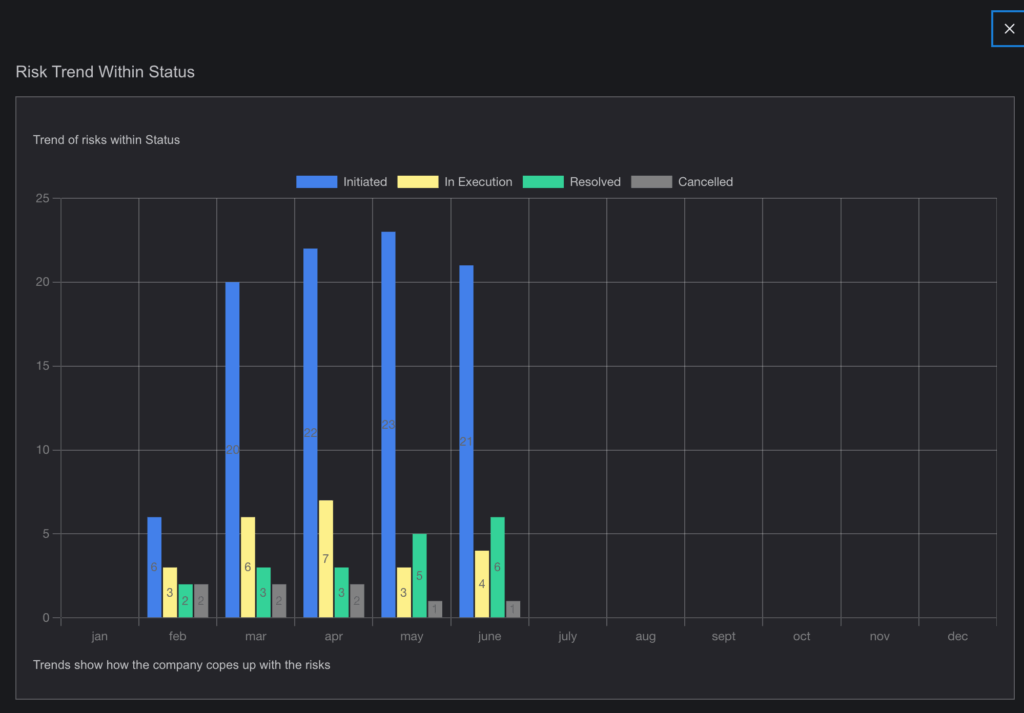
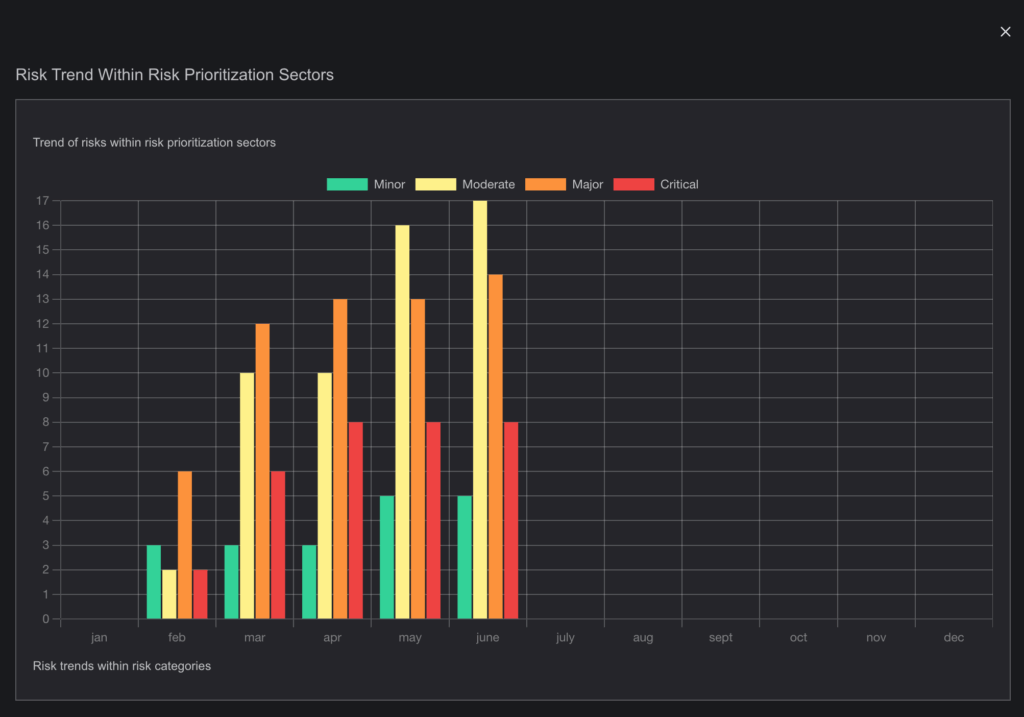
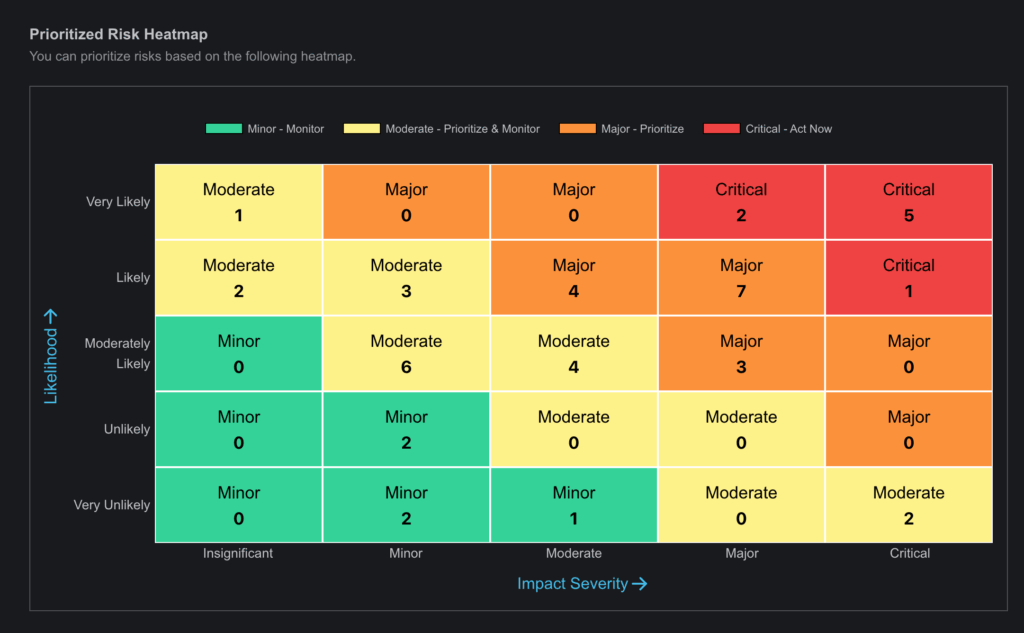

- Dynamic Risk Management:
- Users can adjust priorities as new information arises, ensuring risk management strategies stay dynamic and effective.
- Table View:
- A detailed table view is available, similar to the Risk Register table, containing all risks with relevant information, including priority levels.
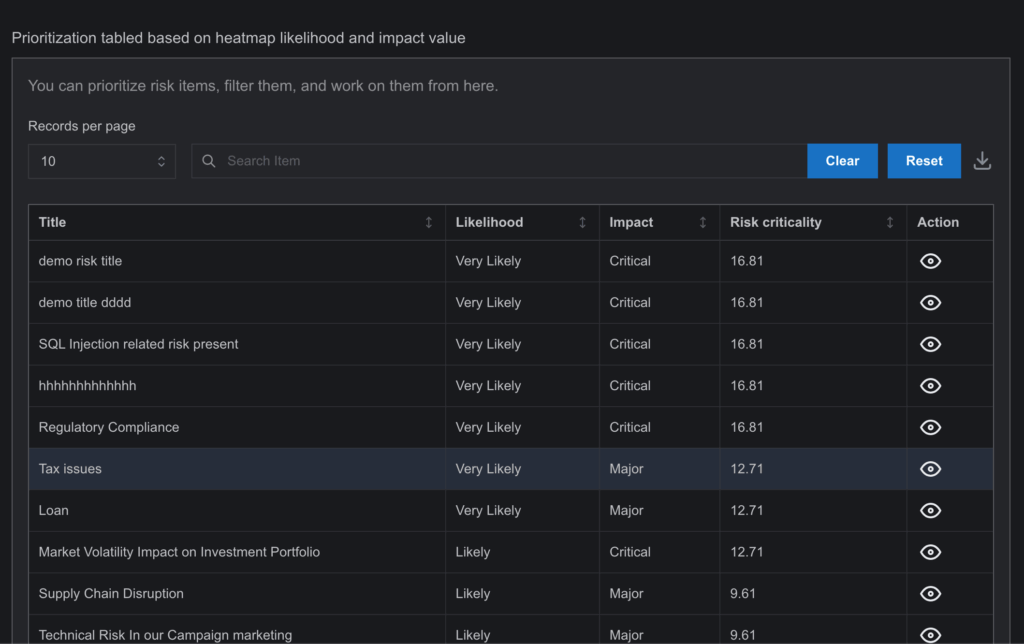
By integrating these features, both the Risk Register and Risk Prioritization Pages offer a complete toolkit for efficient risk tracking, management, and prioritization, ensuring that organizations can mitigate critical risks while maintaining full oversight of their activities.
