-
FAQs
-
Sysrisk User Manual
-
- Getting Started
- Product Catalogue
- Purchase Process
- Login Process and Forgotten Password Revival Process
- User Creation and Role Assignment
- Customization and Dashboard Configuration
- Project Creation and User Adding Process
- Category Management
- Risk Entry Creation, Edit, and Approval
- Risk Creation Using AI
- Risk Approval Process
- Functionality of Risk Register & Risk Prioritization Page
- Issue creation
- Risk Logs: Administrative and User
- Risk Closure Complete Procedure
- Risk Notification Settings
- Support and Knowledge Base
- Company Profile And AI Risk Creation
- Risk Audit
- Show Remaining Articles (4) Collapse Articles
-
-
Risk Management
-
- Control Risk
- Enterprise Risk Management (ERM)
- Inherent Risk
- Qualitative Risk Analysis
- Quantitative Risk Analysis
- Residual Risk
- Risk Acceptance
- Risk Acceptance Criteria
- Risk Aggregation
- Risk Analysis
- Risk Analysis Methods
- Risk Analytics
- Risk Appetite
- Risk Appetite Framework
- Risk Appetite Statement
- Risk Appetite Statement
- Risk Assessment
- Risk Assessment Matrix
- Risk Assessment Process
- Risk Attribution
- Risk Avoidance
- Risk Bearing Capacity
- Risk Benchmarking
- Risk Capacity
- Risk Capital
- Risk Clustering
- Risk Communication
- Risk Communication Plan
- Risk Concentration
- Risk Contingency
- Risk Contingency Plan
- Risk Control
- Risk Convergence
- Risk Criteria
- Risk Culture
- Risk Dashboard
- Risk Dependency
- Risk Diversification
- Risk Escalation
- Risk Escalation Path
- Risk Evaluation
- Risk Exposure
- Risk Financing
- Risk Framework
- Risk Governance
- Risk Heat Map
- Risk Horizon
- Risk Identification
- Risk Indicator
- Risk Intelligence
- Risk Interdependency
- Risk Inventory
- Risk Landscape
- Risk Management(RM)
- Risk Management Dashboard
- Risk Management Framework
- Risk Management Maturity
- Risk Management Plan
- Risk Management Policy
- Risk Mapping
- Risk Matrix
- Risk Maturity
- Risk Mitigation
- Risk Mitigation Plan
- Risk Mitigation Strategy
- Risk Model
- Risk Monitoring
- Risk Optimization
- Risk Owner
- Risk Ownership
- Risk Policy
- Risk Portfolio
- Risk Prioritization
- Risk Profile
- Risk Quantification
- Risk Reduction
- Risk Register
- Risk Register Update
- Risk Reporting
- Risk Resilience
- Risk Response
- Risk Response Plan
- Risk Review
- Risk Review Process
- Risk Scenario
- Risk Scenario Analysis
- Risk Scenario Planning
- Risk Scoring
- Risk Sensing
- Risk Sharing
- Risk Strategy
- Risk Taxonomy
- Risk Threshold
- Risk Tolerance
- Risk Tolerance Level
- Risk Transfer
- Risk Transparency
- Risk-Adjusted Return
- Show Remaining Articles (83) Collapse Articles
-
- Business Continuity Risk
- Capital Risk
- Competition Risk
- Compliance Risk
- Counterparty Risk
- Credit Risk
- Credit Spread Risk
- Currency Risk
- Cybersecurity Risk
- Cybersecurity Risk
- Deflation Risk
- Environmental Risk
- Environmental Risk
- Ethical Risk
- Event Risk
- Financial Risk
- Foreign Exchange Risk
- Fraud Risk
- Fraud Risk
- Geopolitical Risk
- Health and Safety Risk
- Human Capital Risk
- Inflation Risk
- Inflation Risk
- Infrastructure Risk
- Innovation Risk
- Innovation Risk
- Insurance Risk
- Intellectual Property Risk
- Interest Rate Risk
- Legal Risk
- Liquidity Risk
- Liquidity Risk
- Market Risk
- Model Risk
- Natural Disaster Risk
- Operational Risk
- Operational Risk
- Outsourcing Risk
- Political Risk
- Product Liability Risk
- Project Risk
- Regulatory Change Risk
- Regulatory Risk
- Reputation Risk
- Reputation Risk
- Reputational Risk
- Resource Risk
- Sovereign Risk
- Strategic Alliance Risk
- Strategic Risk
- Strategic Risk
- Supply Chain Risk
- Sustainability Risk
- Systemic Risk
- Technological Risk
- Technology Risk
- Show Remaining Articles (42) Collapse Articles
-
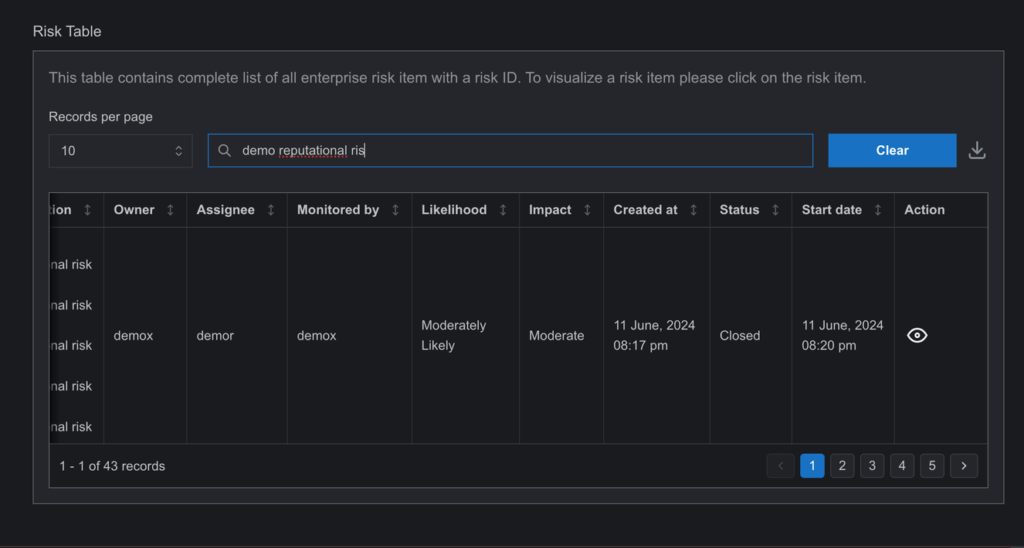
Closing a risk is a more complex procedure compared to updating other risk activity statuses. It resembles the process of approving a risk item, as both require multiple levels of approval. Because recording and managing a risk item in the software demands various approvals, closing a risk entry also necessitates several approvals. Therefore, unlike other status updates, we provide a dedicated page for risk closure due to the intricate nature of the process.
Step-by-step Process
1. First, the admin or product admin must log in to their SysRisk account.
2. The user then navigates to their desired product (ERM or PRM).
3. Moving to the Products(ERM or PRM) will display the product options, from which the user must go to the Workflow page.
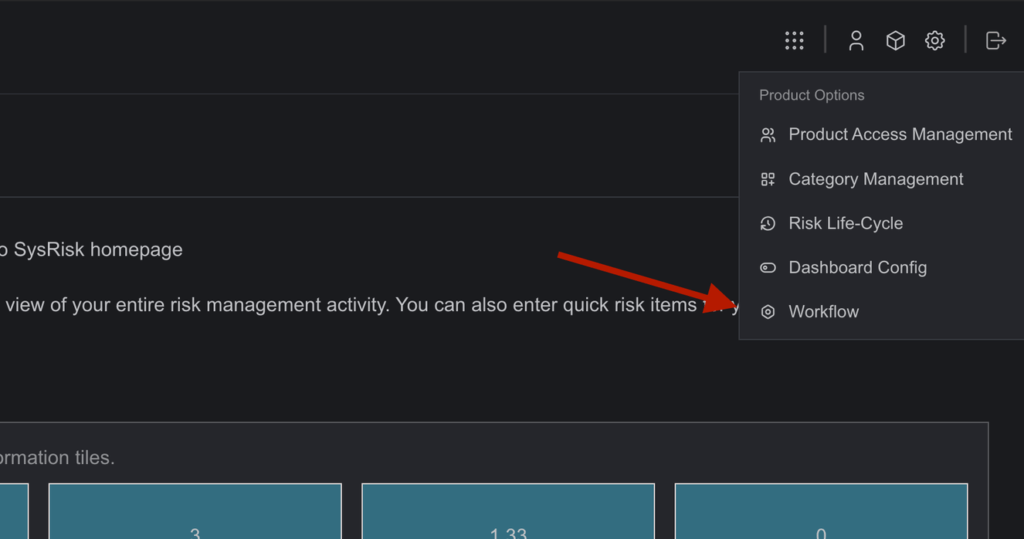
4. On the Workflow page, the user will find a table named “List of Enterprise Workflows.” In the table, on the right side of “Enterprise Risk Closure Workflow,” a user icon will be visible.
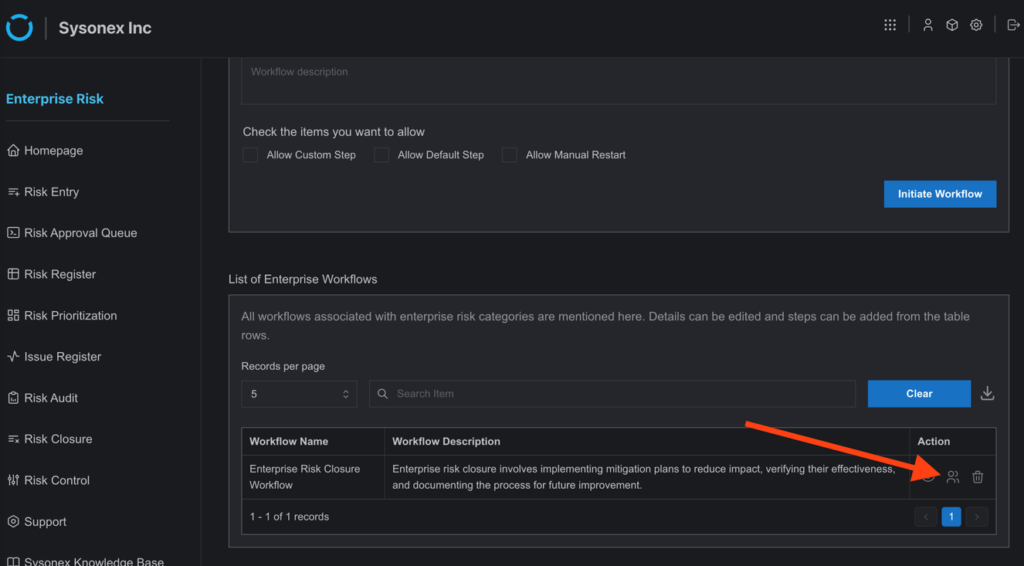
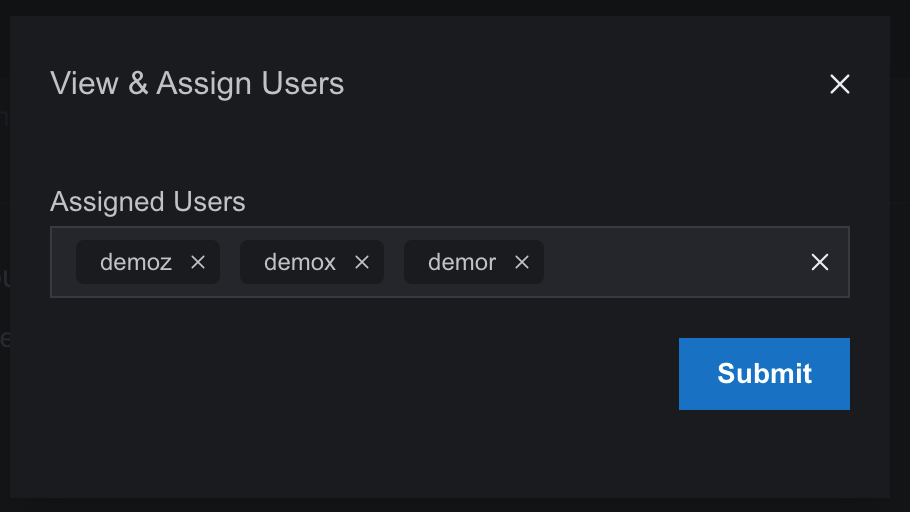
5. Clicking on that icon will show a box with the names of users already in the workflow, along with a dropdown menu to add other users to the workflow. Add the desired users and press submit.
6. Now, if someone associated with a risk closes a risk on the Risk Register page after resolving it, the status will be marked as “resolved”.
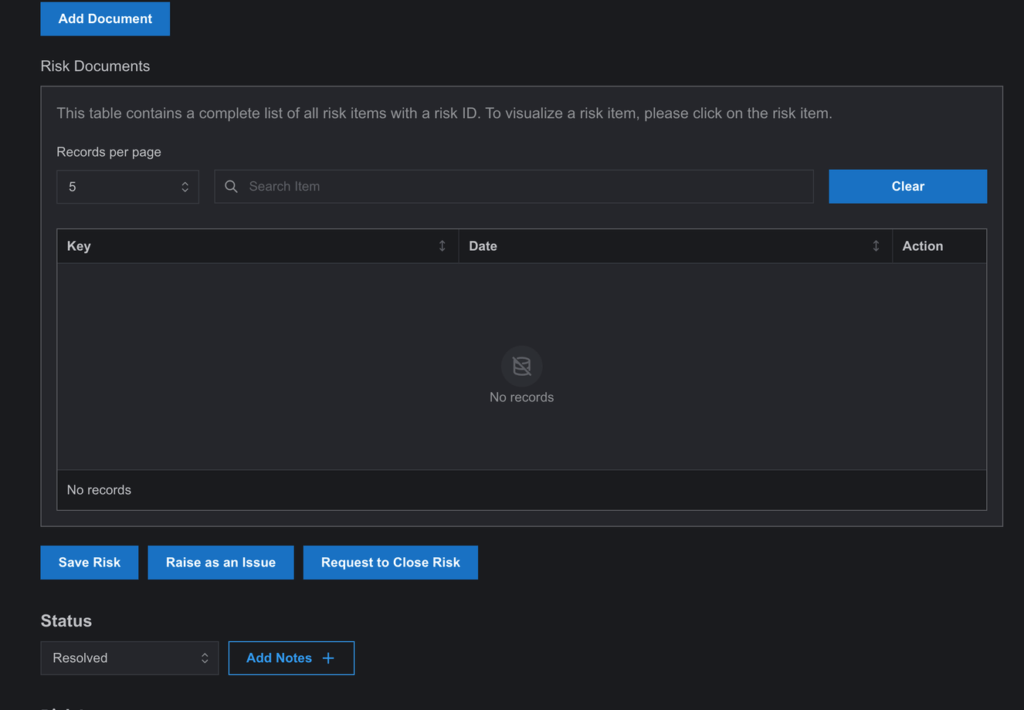
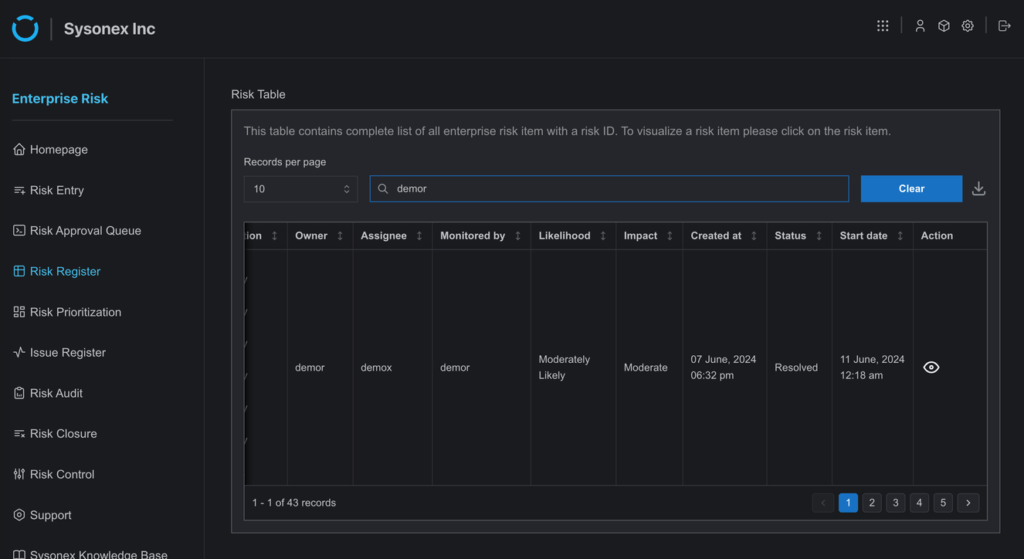
7. The risk item will be sent to the users added to the risk closure workflow, and it will appear on their Risk Closure page with an “Initiated” status, indicating the beginning of the risk closure process.
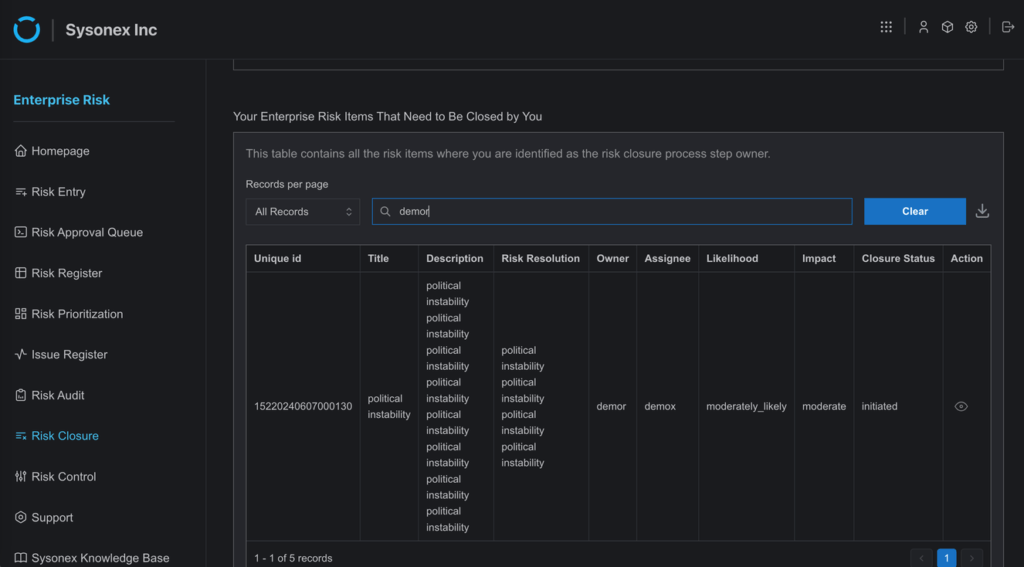
8. Those users must then fill in the form to execute the process. If any one of the users fills in the form, the risk entry becomes eligible for closing. Users also have the authority to “Reject” or “Request for Change” options besides “Close,” similar to the Risk Approval process.
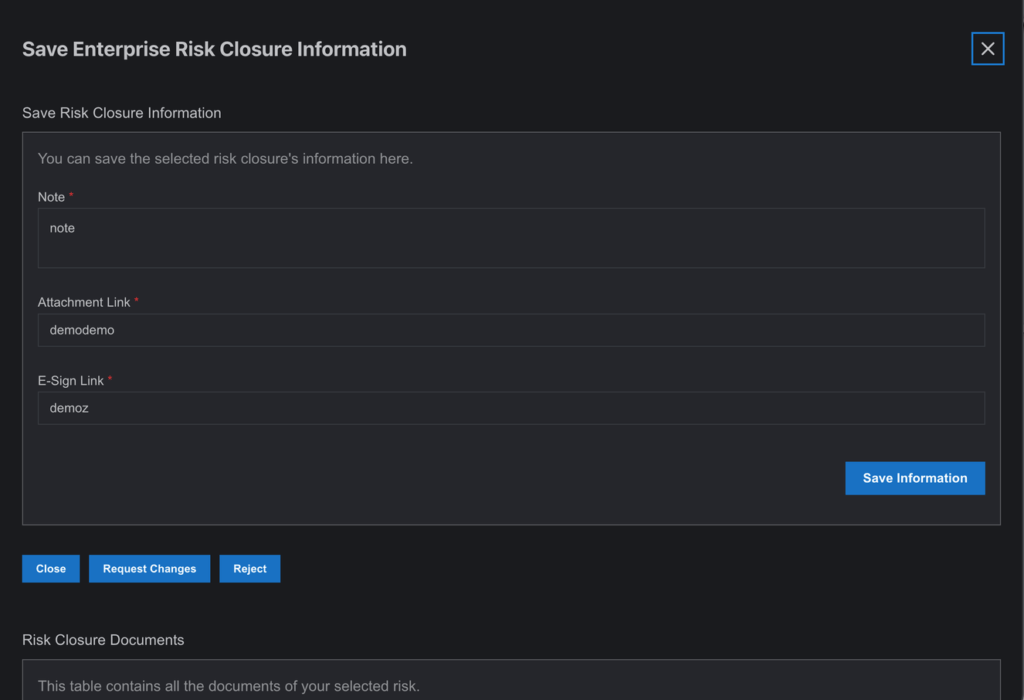
9. If there are multiple users in the workflow after one user closes the risk item, the status of the risk item updates to “Partially Completed” on the Risk Closure page and “Partially Closed” in the Risk Register page. Only if all of the users (associated with the workflow) close the risk in their Risk Closure page will the activity status be “Completed” on the Risk Closure page and “Closed” on the Risk Register page. The risk will then move to the Risk Register from Risk Closure as a closed risk for several years.