How Can We Help?
-
FAQs
-
Sysrisk User Manual
-
- Getting Started
- Product Catalogue
- Purchase Process
- Login Process and Forgotten Password Revival Process
- User Creation and Role Assignment
- Customization and Dashboard Configuration
- Project Creation and User Adding Process
- Category Management
- Risk Entry Creation, Edit, and Approval
- Risk Creation Using AI
- Risk Approval Process
- Functionality of Risk Register & Risk Prioritization Page
- Issue creation
- Risk Logs: Administrative and User
- Risk Closure Complete Procedure
- Risk Notification Settings
- Support and Knowledge Base
- Company Profile And AI Risk Creation
- Risk Audit
- Show Remaining Articles (4) Collapse Articles
-
-
Risk Management
-
- Control Risk
- Enterprise Risk Management (ERM)
- Inherent Risk
- Qualitative Risk Analysis
- Quantitative Risk Analysis
- Residual Risk
- Risk Acceptance
- Risk Acceptance Criteria
- Risk Aggregation
- Risk Analysis
- Risk Analysis Methods
- Risk Analytics
- Risk Appetite
- Risk Appetite Framework
- Risk Appetite Statement
- Risk Appetite Statement
- Risk Assessment
- Risk Assessment Matrix
- Risk Assessment Process
- Risk Attribution
- Risk Avoidance
- Risk Bearing Capacity
- Risk Benchmarking
- Risk Capacity
- Risk Capital
- Risk Clustering
- Risk Communication
- Risk Communication Plan
- Risk Concentration
- Risk Contingency
- Risk Contingency Plan
- Risk Control
- Risk Convergence
- Risk Criteria
- Risk Culture
- Risk Dashboard
- Risk Dependency
- Risk Diversification
- Risk Escalation
- Risk Escalation Path
- Risk Evaluation
- Risk Exposure
- Risk Financing
- Risk Framework
- Risk Governance
- Risk Heat Map
- Risk Horizon
- Risk Identification
- Risk Indicator
- Risk Intelligence
- Risk Interdependency
- Risk Inventory
- Risk Landscape
- Risk Management(RM)
- Risk Management Dashboard
- Risk Management Framework
- Risk Management Maturity
- Risk Management Plan
- Risk Management Policy
- Risk Mapping
- Risk Matrix
- Risk Maturity
- Risk Mitigation
- Risk Mitigation Plan
- Risk Mitigation Strategy
- Risk Model
- Risk Monitoring
- Risk Optimization
- Risk Owner
- Risk Ownership
- Risk Policy
- Risk Portfolio
- Risk Prioritization
- Risk Profile
- Risk Quantification
- Risk Reduction
- Risk Register
- Risk Register Update
- Risk Reporting
- Risk Resilience
- Risk Response
- Risk Response Plan
- Risk Review
- Risk Review Process
- Risk Scenario
- Risk Scenario Analysis
- Risk Scenario Planning
- Risk Scoring
- Risk Sensing
- Risk Sharing
- Risk Strategy
- Risk Taxonomy
- Risk Threshold
- Risk Tolerance
- Risk Tolerance Level
- Risk Transfer
- Risk Transparency
- Risk-Adjusted Return
- Show Remaining Articles (83) Collapse Articles
-
- Business Continuity Risk
- Capital Risk
- Competition Risk
- Compliance Risk
- Counterparty Risk
- Credit Risk
- Credit Spread Risk
- Currency Risk
- Cybersecurity Risk
- Cybersecurity Risk
- Deflation Risk
- Environmental Risk
- Environmental Risk
- Ethical Risk
- Event Risk
- Financial Risk
- Foreign Exchange Risk
- Fraud Risk
- Fraud Risk
- Geopolitical Risk
- Health and Safety Risk
- Human Capital Risk
- Inflation Risk
- Inflation Risk
- Infrastructure Risk
- Innovation Risk
- Innovation Risk
- Insurance Risk
- Intellectual Property Risk
- Interest Rate Risk
- Legal Risk
- Liquidity Risk
- Liquidity Risk
- Market Risk
- Model Risk
- Natural Disaster Risk
- Operational Risk
- Operational Risk
- Outsourcing Risk
- Political Risk
- Product Liability Risk
- Project Risk
- Regulatory Change Risk
- Regulatory Risk
- Reputation Risk
- Reputation Risk
- Reputational Risk
- Resource Risk
- Sovereign Risk
- Strategic Alliance Risk
- Strategic Risk
- Strategic Risk
- Supply Chain Risk
- Sustainability Risk
- Systemic Risk
- Technological Risk
- Technology Risk
- Show Remaining Articles (42) Collapse Articles
-
Risk Register Page
The Risk Register page is a centralized repository where all approved risk entries are stored. Each entry is assigned a unique ID upon approval, allowing for easy tracking and management. This page consolidates all risk data, providing a comprehensive view of active risks, their statuses, and associated details. It serves as a critical component for monitoring, updating, and analysing risks, ensuring that all relevant information is accessible for informed decision-making and future problem-solving. Admins and Product admins can see all the risk items that have been created in that module. On the other hand, general users can only see and access to the risks that he is a part of.
Features
- All approved risks and their complete information are stored here.
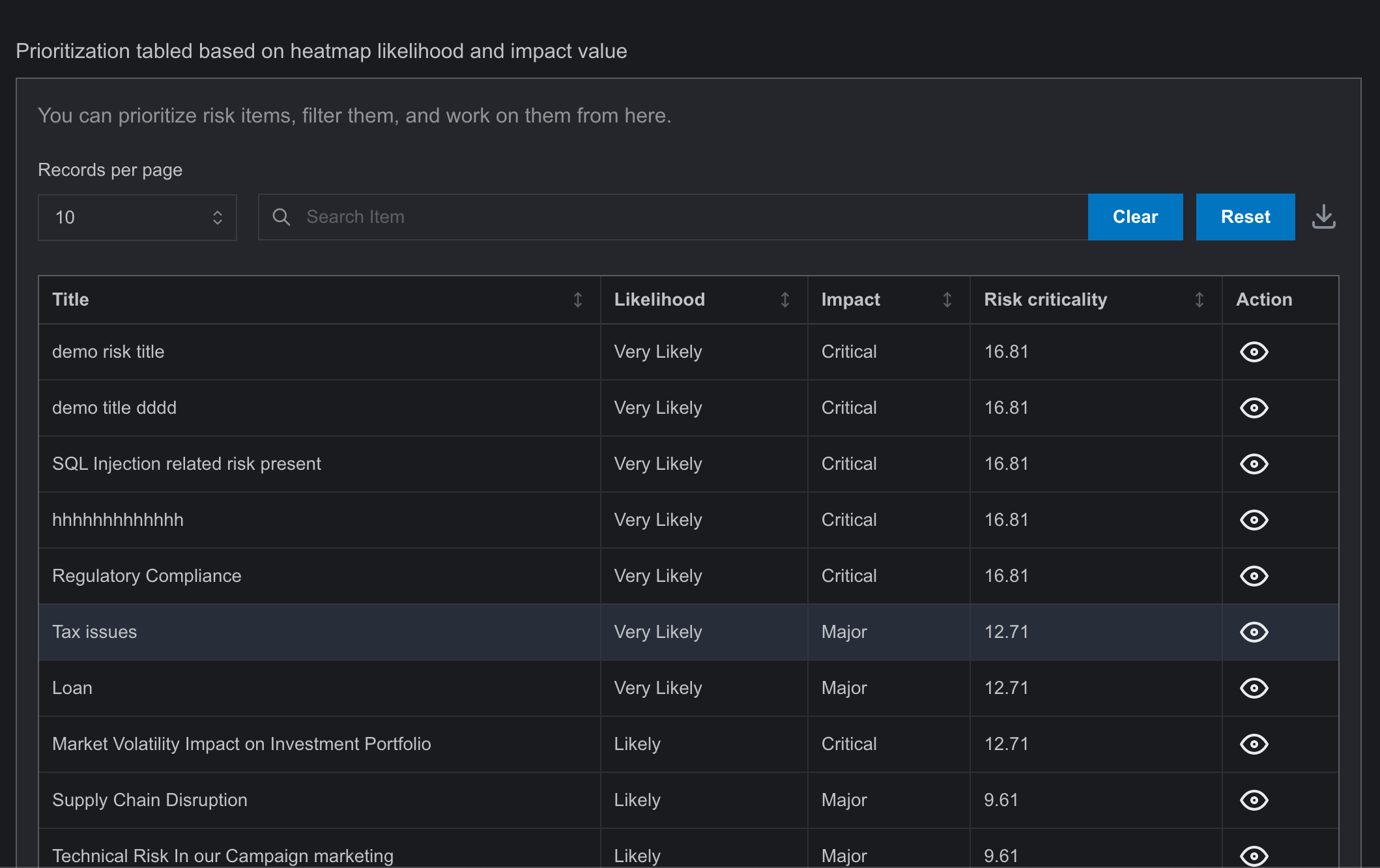
- Risks can be filtered by their categories and activity status, and a search option is available..
- Once recorded in the Risk Register page, a risk cannot be deleted, but it can be edited.
- When a risk is first approved, it is in the “Initiated” state.
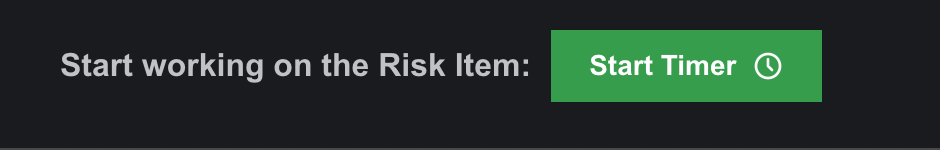
- To update the activity status, users must access the Start Timer option in the editing sub-page.
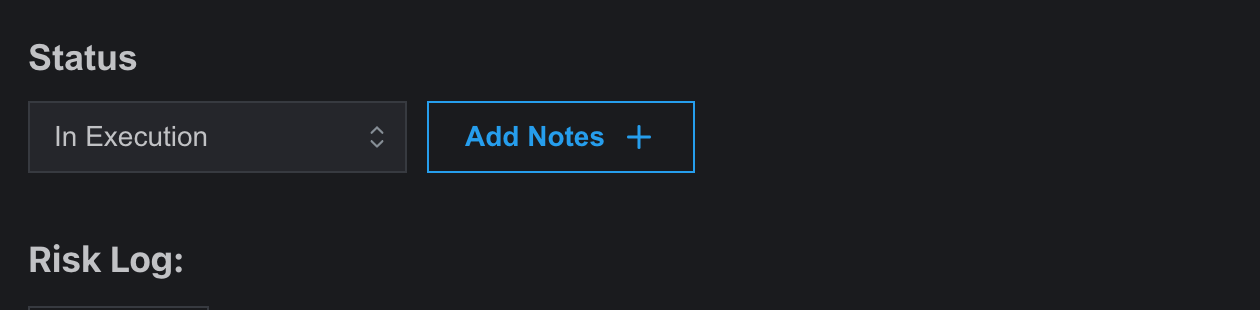
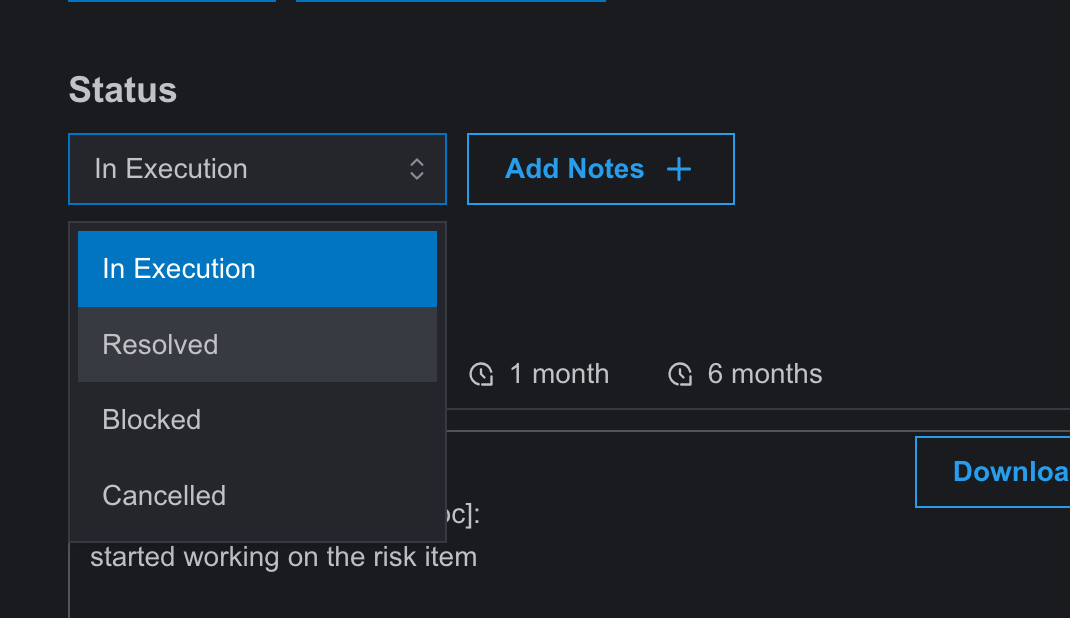
- After starting the timer, the risk item’s status updates to “In Execution” from “Initiated.” Users can also update the status manually.
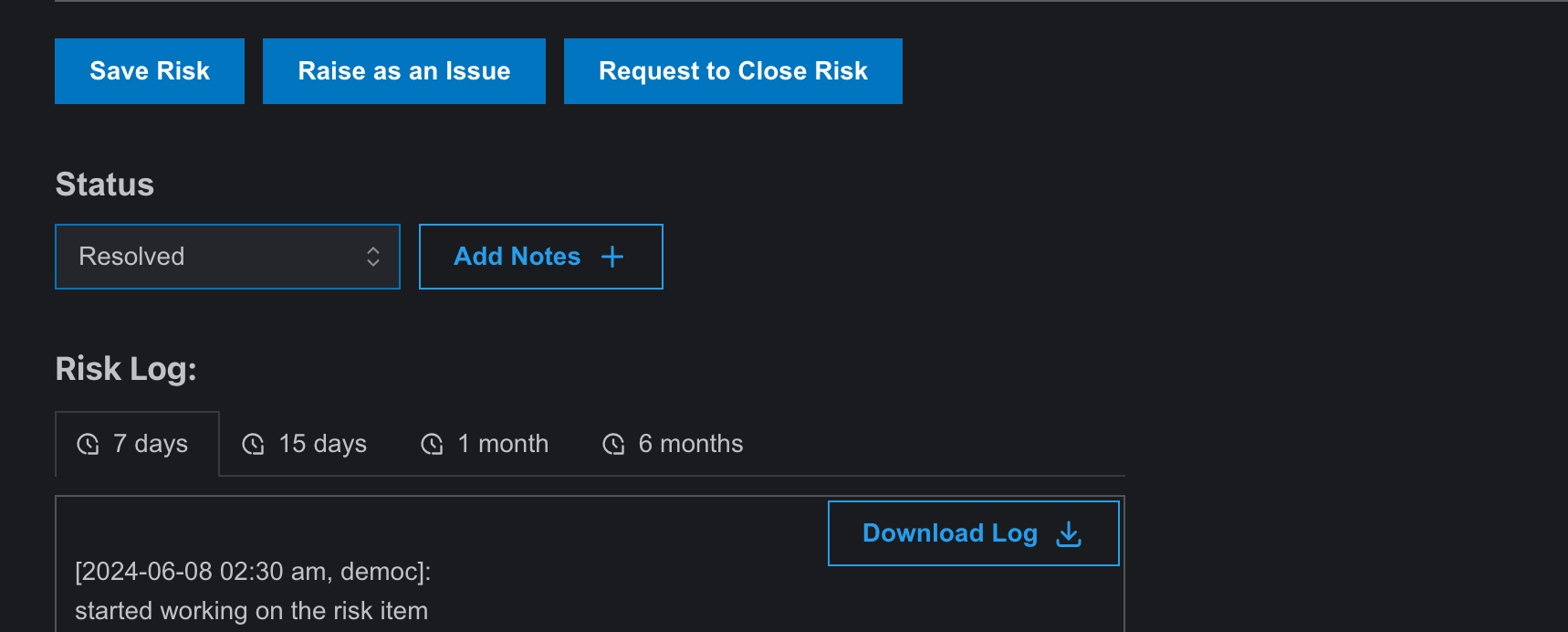
- To close a risk, the user must update the status to “Resolved” and then request for closure. The user assigned to the risk closure workflow must then close the risk, updating the status to “closed.” Until then, it will show as partially closed.
- Once closed, a risk will remain in the register record for seven years.
- A note adding feature is also added for suggestions and corrections from teammates.
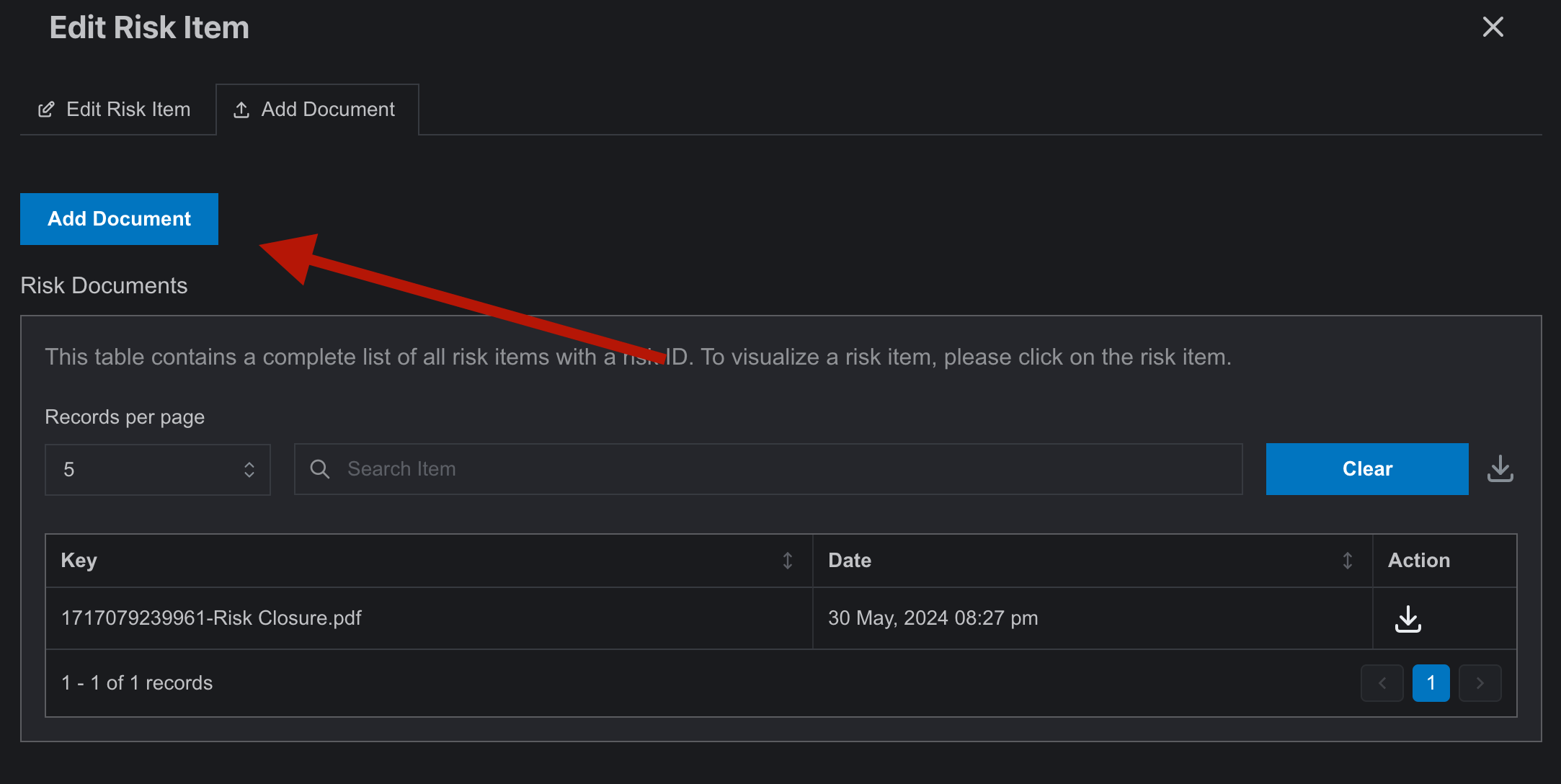
- Users can add documents to the risk item for future reference by navigating to the Add Document tab.
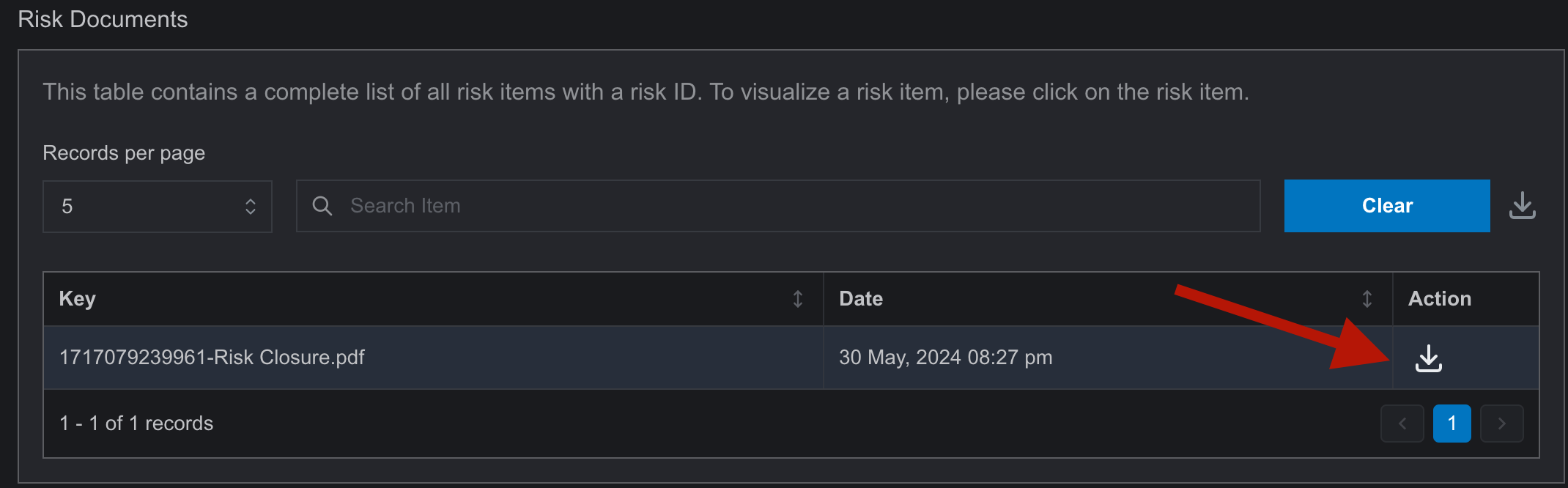
- Documents can be downloaded after uploading for future need.
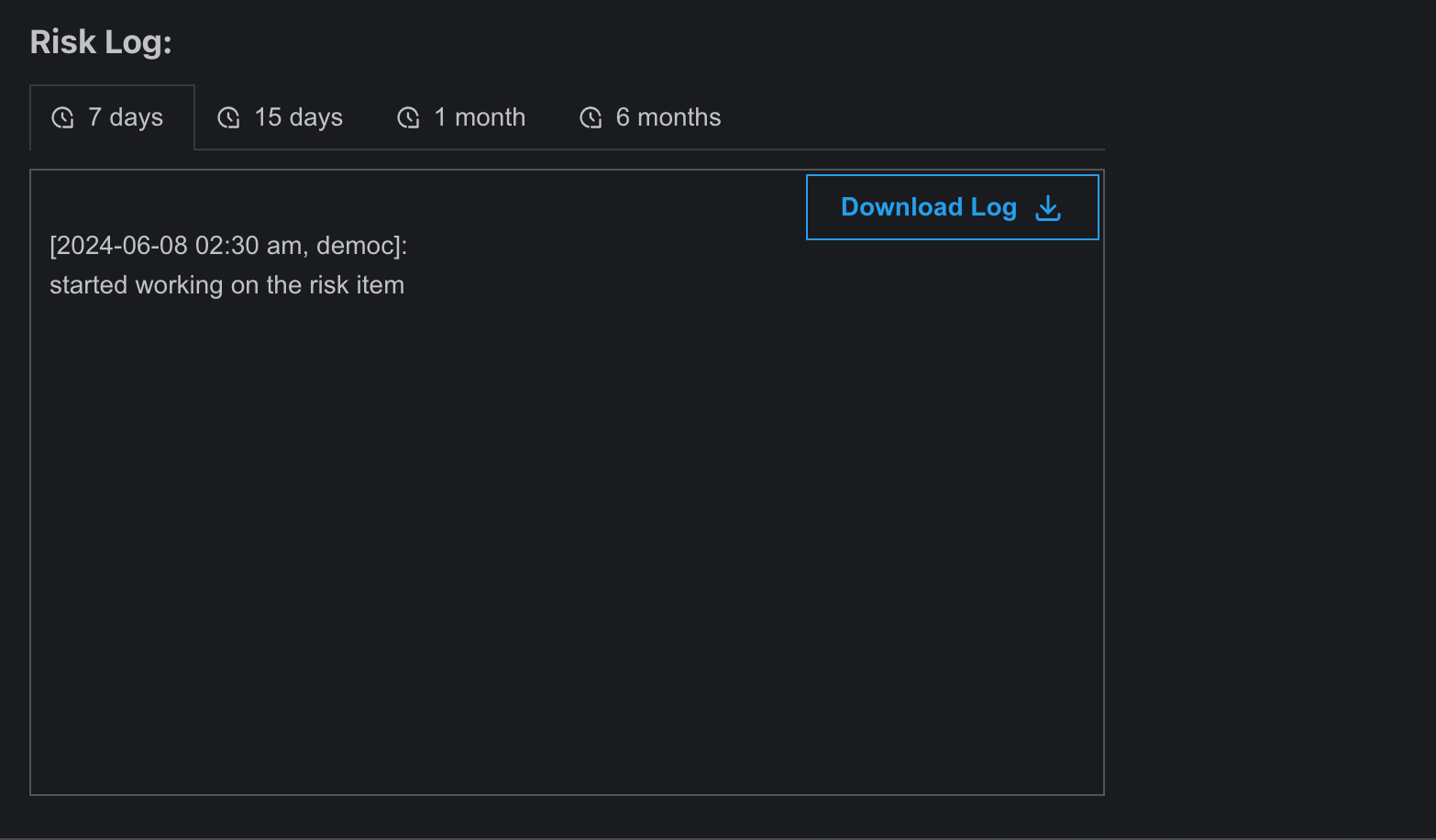
- Here is also a Risk Log where every small acts that has been conducted on this entry is recorded.
- Users can convert a risk item into an issue item directly from the Risk Register page.


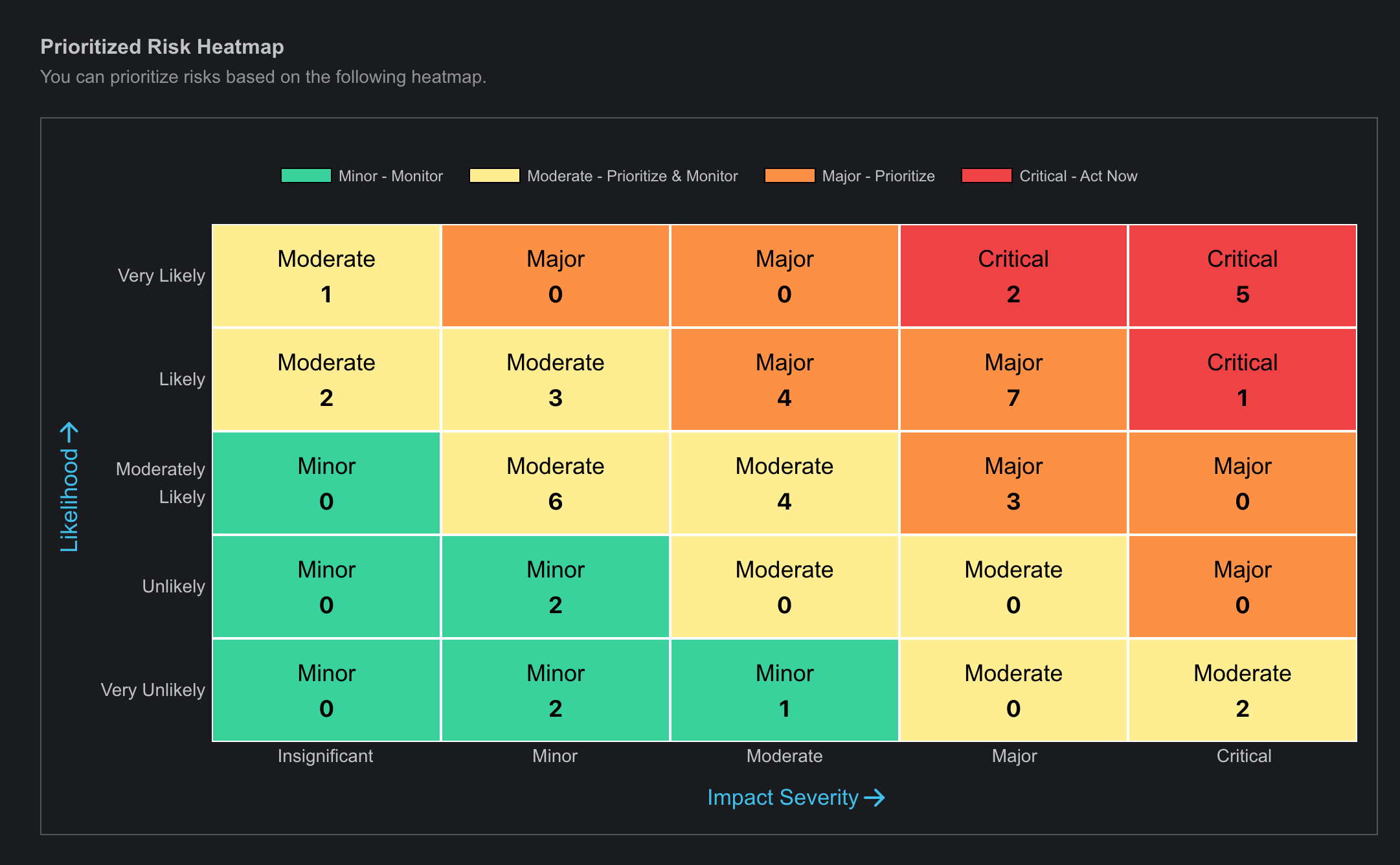
Risk Prioritization Page
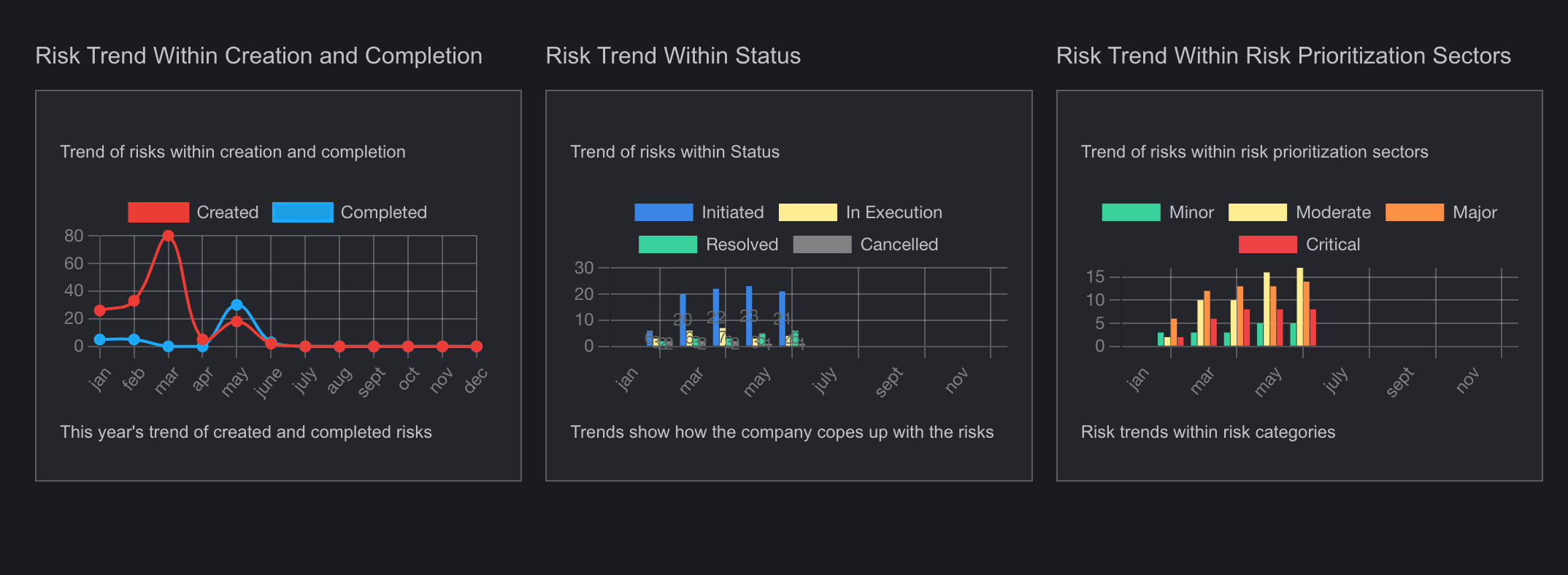
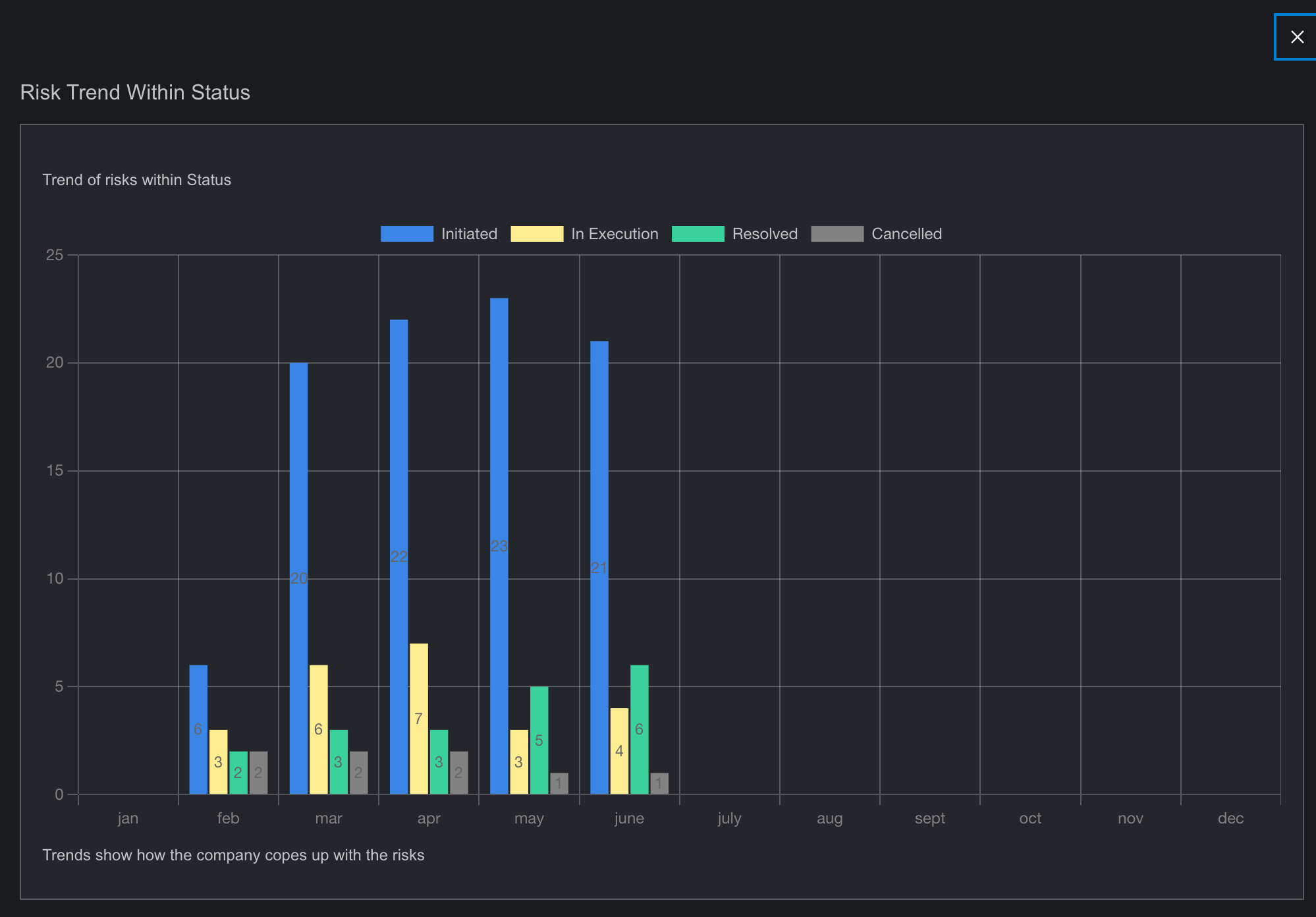
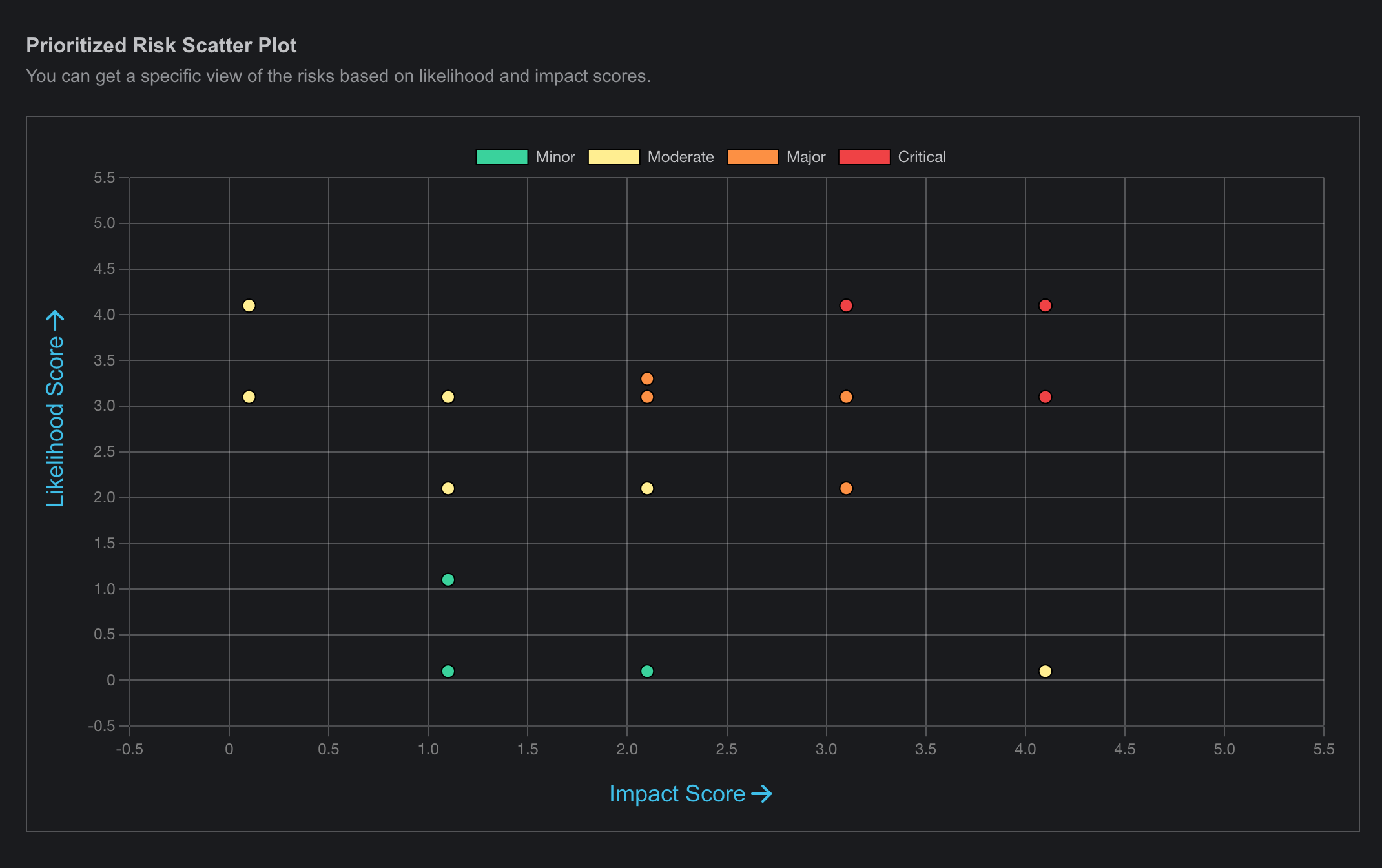
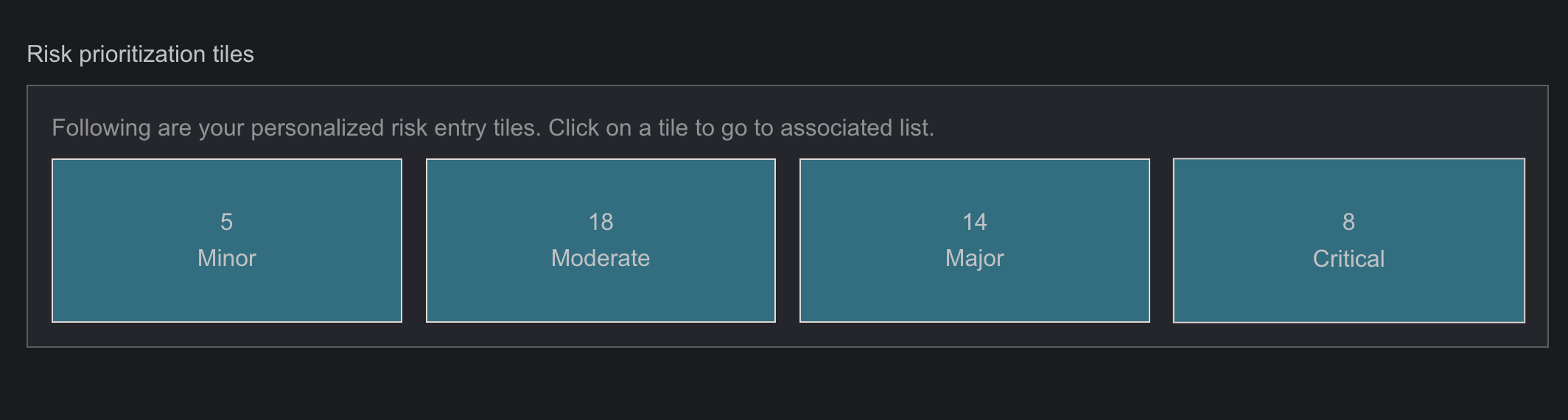
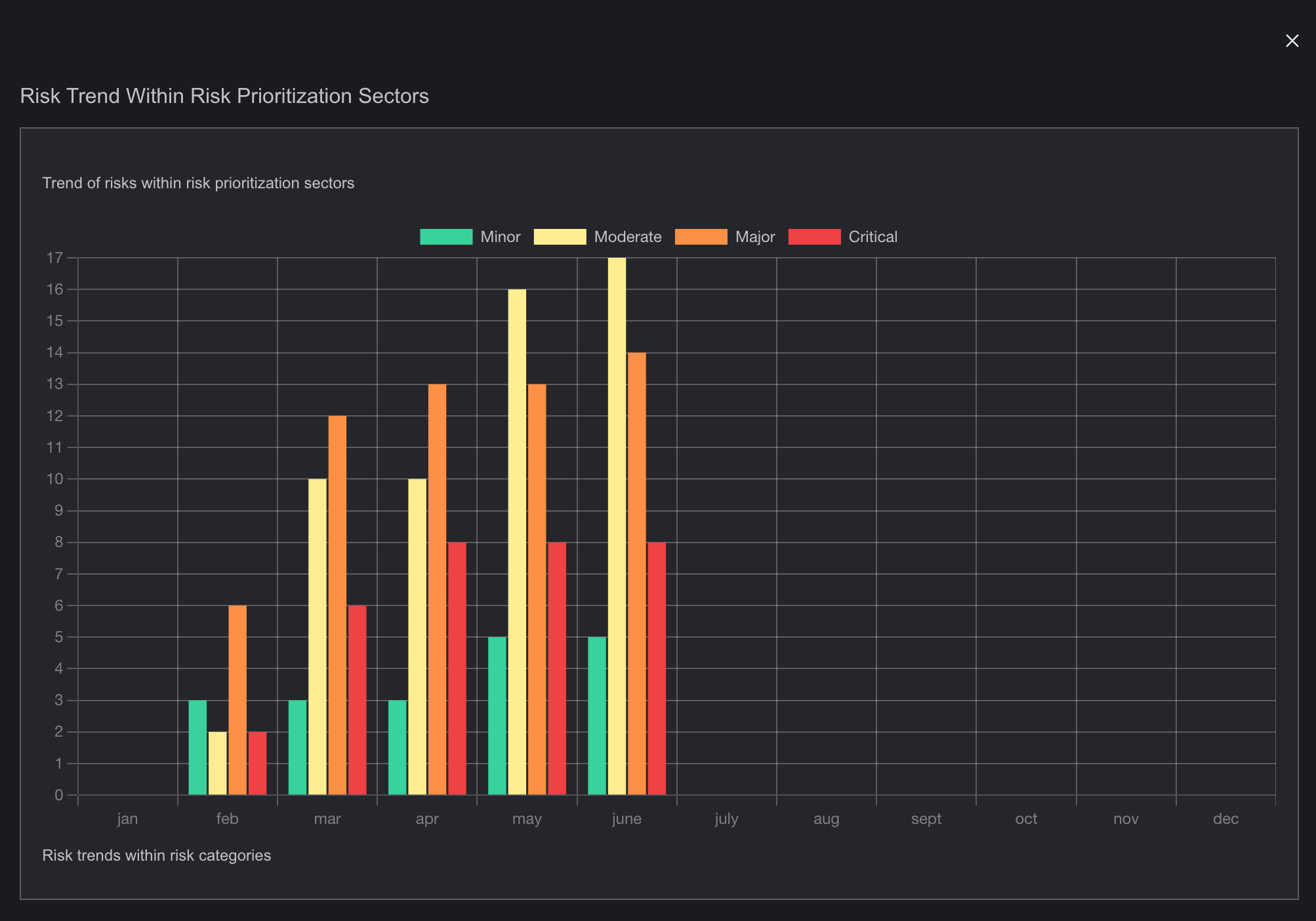
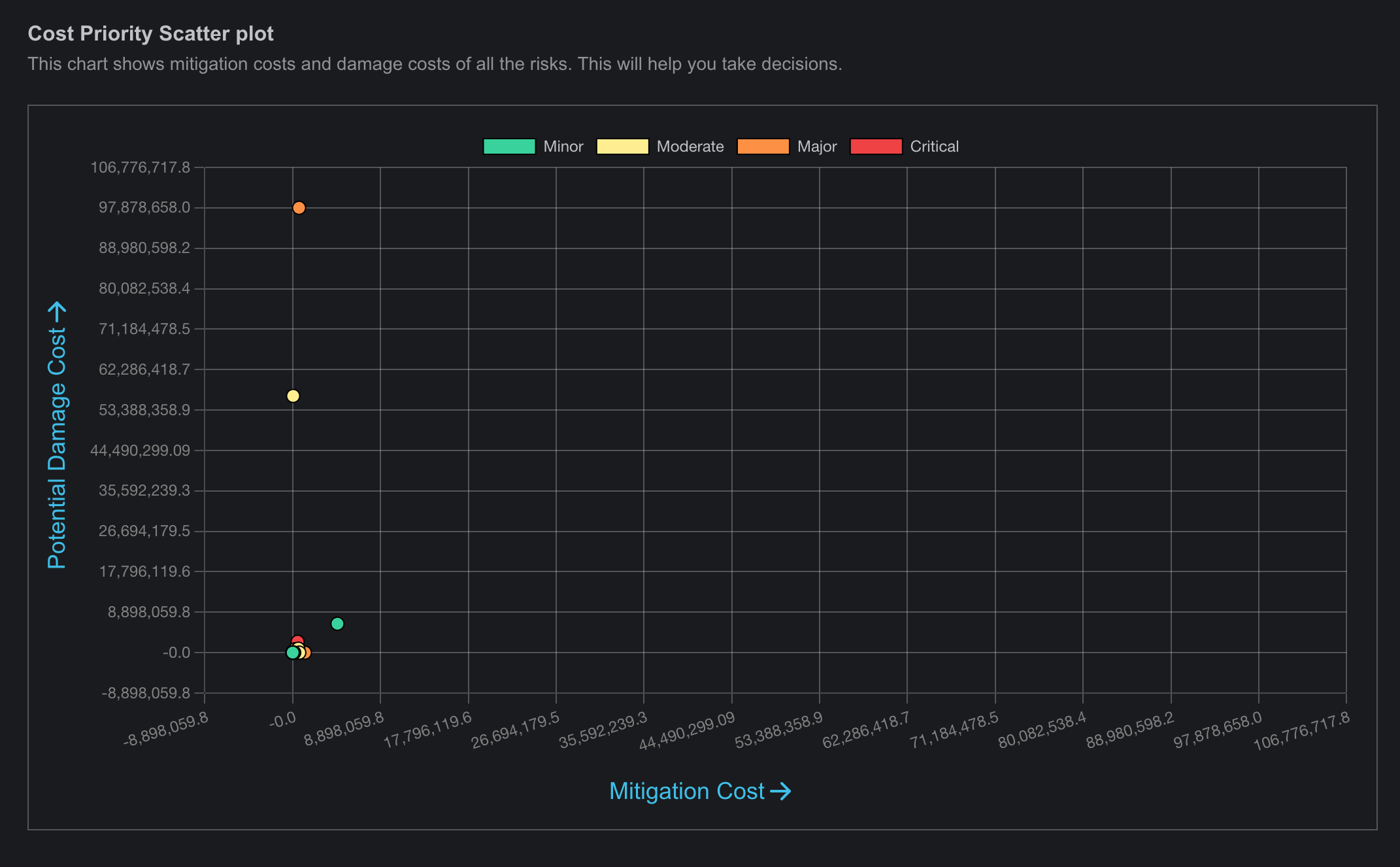
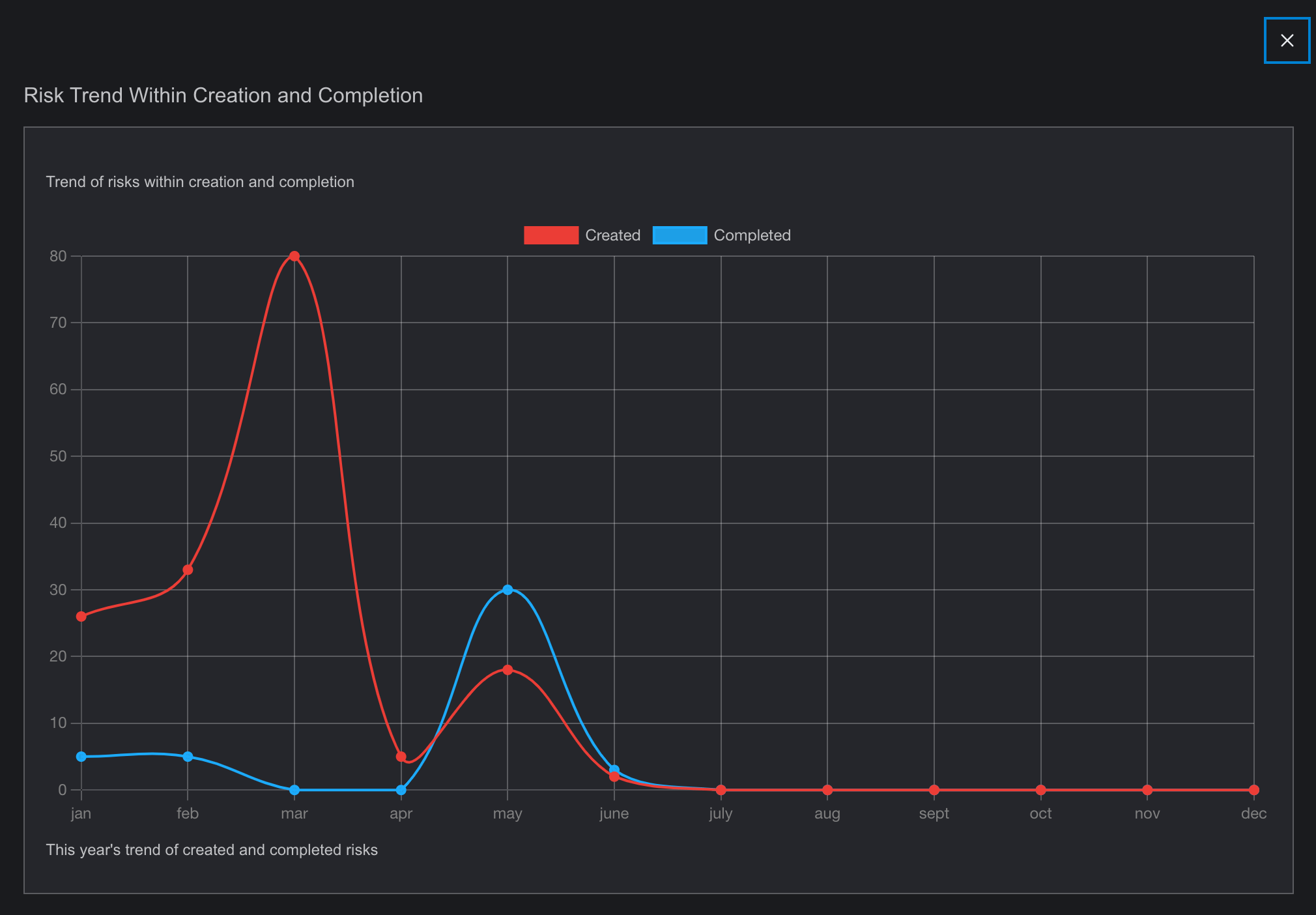
The Risk Prioritization page is a crucial tool for managing and assessing the relative importance of identified risks. This page enables users to rank risks based on various criteria such as impact, likelihood, and cost priority. By providing a clear overview of which risks require immediate attention and resources, the Risk Prioritization page helps organizations focus their efforts on mitigating the most critical threats by presenting data with various graph, heat maps and table. It also allows for the adjustment of priorities as new information becomes available, ensuring that risk management strategies remain dynamic and effective.
Features
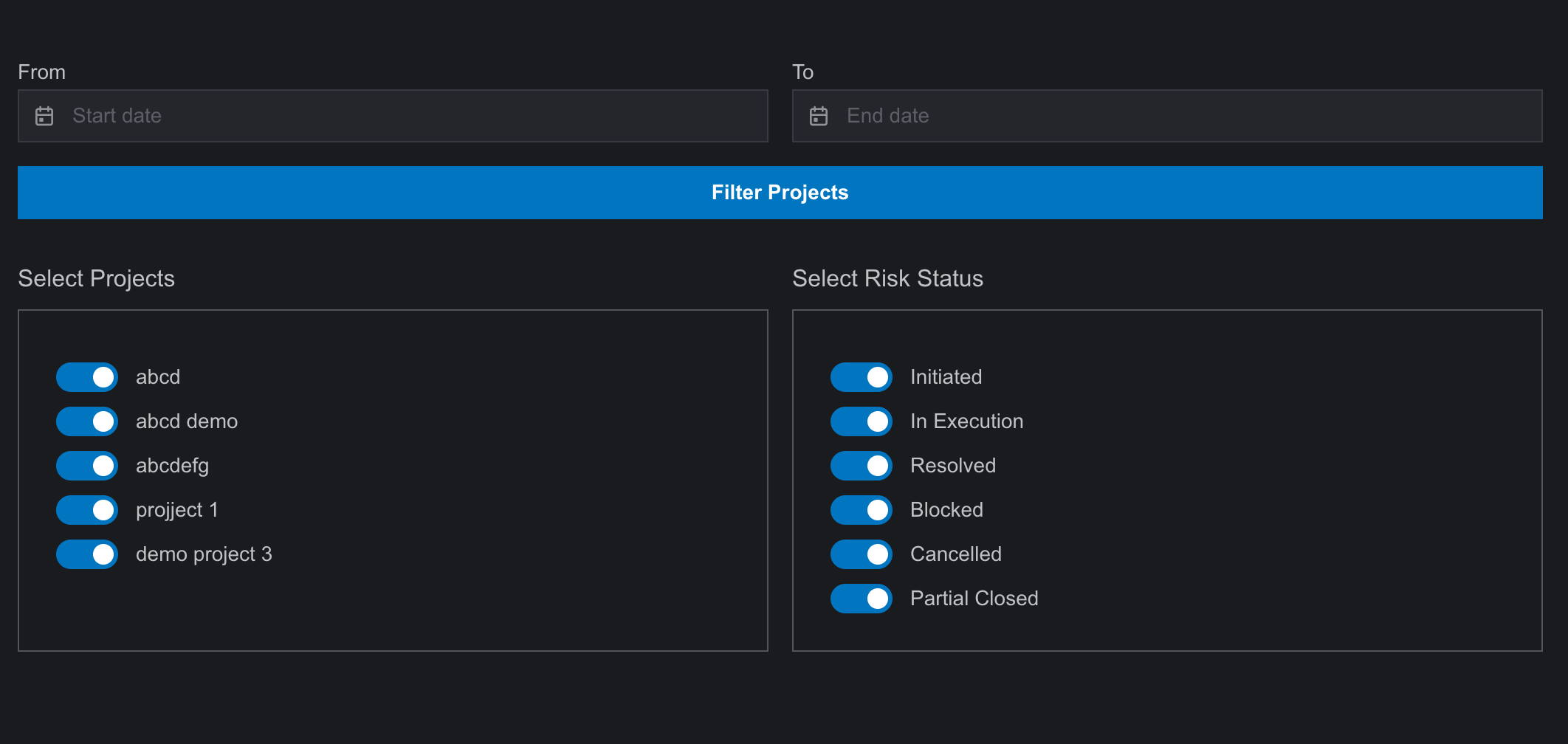
- In the PRM module, a time filter is available to filter projects by specific time periods. Additionally, project and risk status toggle filters are provided for a more organized page visualization.
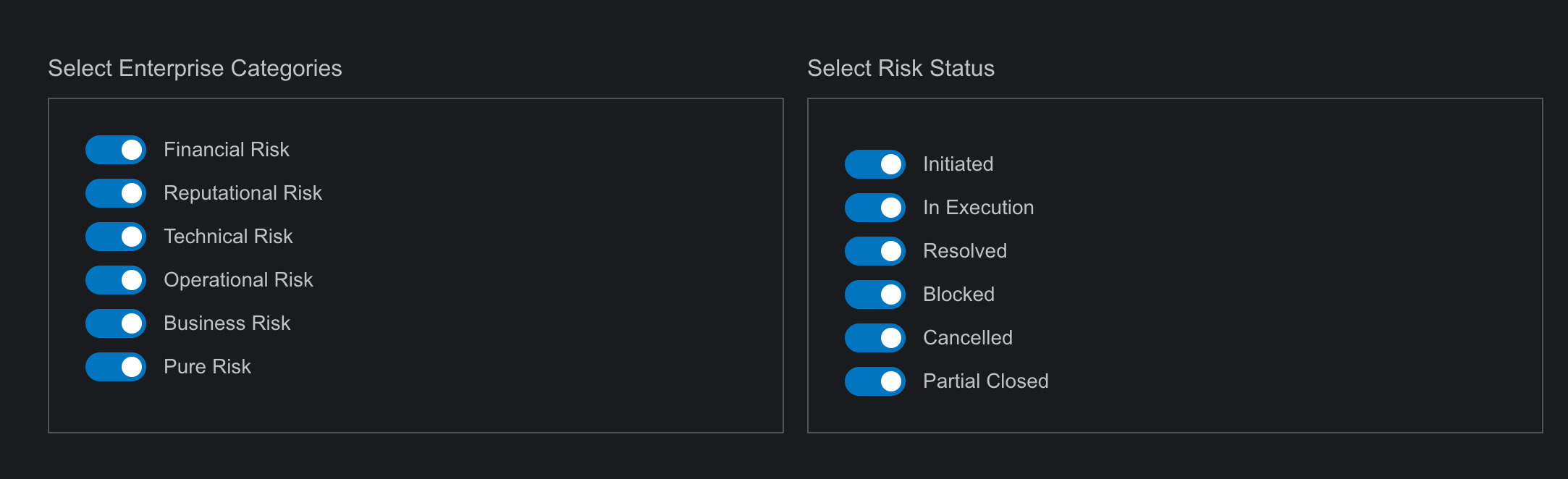
- In the ERM module, SysRisk offers category and activity status filters.
- This page provides a comprehensive visualization of prioritized risks based on different units, featuring various graphical representations.
- A table containing all risks and their definitive information is also available on this page. and the functionality of this table is similar to Risk Register page table..